Network Packet Brokers
Network Packet Brokers (NPBs) make monitoring and security tools more effective, by giving them access to a range of data from across the entire network. Blind spots are reduced, giving tools the visibility they need to identify and tackle performance and security threats.
Network Packet Broker Features
The Cybereason Defense Platform moves beyond endless alerting to instead recognize, expose, and end malicious operations before they take hold. The result: Defenders can end attacks in minutes.
Traffic Aggregation
Collect network traffic from multiple links and consolidate it into a single stream, ensuring monitoring and security tools receive a comprehensive view of all network activity.
Traffic Filtering
Selectively forward packets based on defined rules, such as IP address, VLAN, protocol, or application type, reducing unnecessary data and optimizing monitoring tool efficiency.
Load Balancing
Distribute incoming traffic across multiple security and monitoring devices, prevent overload on any single tool and enhance efficiency, scalability, and network reliability.
Deduplication
Eliminate redundant packets before sending them to security and analytics tools, reducing processing load and ensure accurate analysis without wasting bandwidth and storage.
Packet Slicing
Trim unnecessary portions of packets, such as payload data, while retaining critical headers, reducing bandwidth usage and improving processing efficiency for security and monitoring tools.
Packet Masking
Obscure or redact sensitive data, such as personally identifiable information (PII) and financial details, ensuring compliance with data privacy regulations while maintaining network visibility.
Time Stamping
Embed high-precision timestamps into packets, aiding forensic analysis, latency measurements, and event correlation by ensuring accurate sequencing of captured data.
Bypass & Failover Protection
Automatically reroute traffic in case of tool failure or maintenance, ensuring continuous monitoring and preventing network blind spots or disruptions.
Protocol & Application Awareness
Identify and classify network traffic based on protocols and applications, allowing intelligent filtering and forwarding to optimize monitoring tool effectiveness.
The Value of Network Packet Brokers
With network architectures becoming more complex and the proliferation of higher speeds and data volumes, Network Packet Brokers help you optimize the performance of your monitoring and security tools.
NPB's drive value across the entire network by giving each device the correct packet data, which increases network efficiency while reducing your costs.
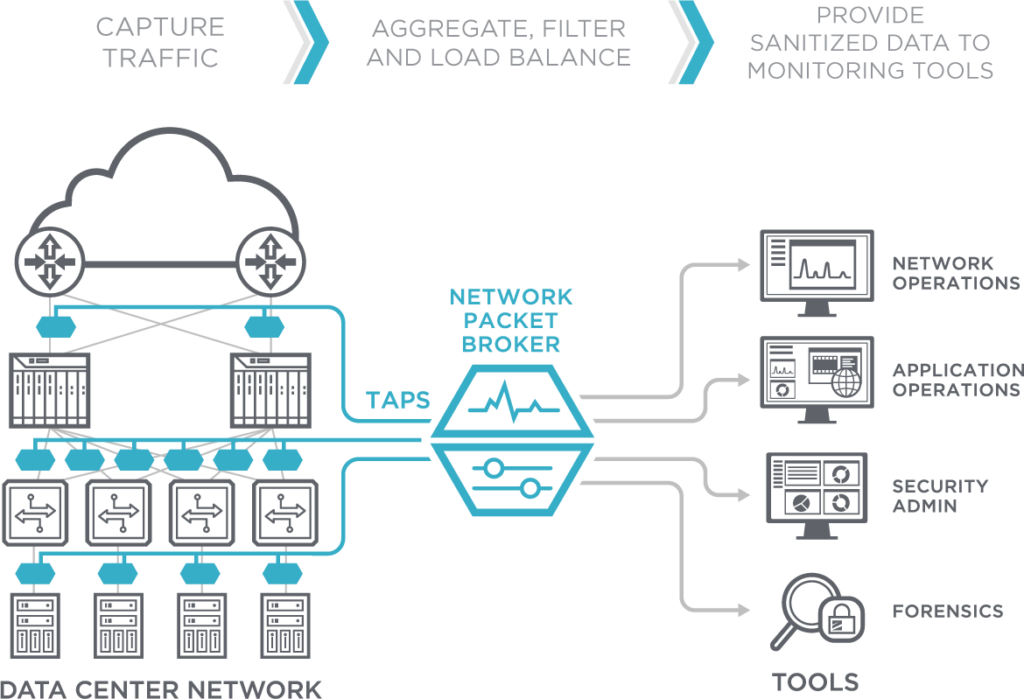
Network Packet Brokers - How can they help you?
The diagram below shows how an NPB receives data from a number of network links. It then acts as a “broker”, ensuring the relevant data is sent to the right tool.