I was recently at a conference where the topic of network security came up again, like it always does. It seems like there might be a little more attention on it now, not really due to the number of breaches—although that plays into a little—but more because companies are being held accountable for allowing the breaches. Examples include Target (where both the CIO and CEO got fired over that breach in 2013) and the fact that the FCC and FTC are fining companies (like YourTel America, TerraCom, Presbyterian Hospital, and Columbia University) that allow a breach to compromise customer data.
This is an area where application intelligence could be used to help IT engineers. Just to be clear, application intelligence won’t fix ALL of your security problems, but it can give you additional and useful information that was very difficult to ascertain before now. For those that haven’t heard about application intelligence, this technology is available through certain network packet brokers (NPBs). It’s an extended functionality that allows you to go beyond Layer 2 through 4 (of the OSI model) packet filtering to reach all the way into Layer 7 (the application layer) of the packet data.
The benefit here is that rich data on the behavior and location of users and applications can be created and exported in any format needed—raw packets, filtered packets, or NetFlow information. IT teams can identify hidden network applications, mitigate network security threats from rogue applications and user types, and reduce network outages and/or improve network performance due to application data information.
 In short, application intelligence is basically the real-time visualization of application level data. This includes the dynamic identification of known and unknown applications on the network, application traffic and bandwidth use, detailed breakdowns of applications in use by application type, and geo-locations of users and devices while accessing applications.
In short, application intelligence is basically the real-time visualization of application level data. This includes the dynamic identification of known and unknown applications on the network, application traffic and bandwidth use, detailed breakdowns of applications in use by application type, and geo-locations of users and devices while accessing applications.
Distinct signatures for known and unknown applications can be identified, captured, and passed on to specialized monitoring tools to provide network managers a complete view of their network. The filtered application information is typically sent on to 3rd party monitoring tools (e.g. Plixer, Splunk, etc.) as NetFlow information but could also be consumed through a direct user interface in the NPB. The benefit to sending the information to 3rd party monitoring tools is that it often gives them more granular, detailed application data than they would have otherwise to improve their efficiency.
With the number of applications on service provider and enterprise networks rapidly increasing, application intelligence provides unprecedented visibility to enable IT organizations to identify unknown network applications. This level of insight helps mitigate network security threats from suspicious applications and locations. It also allows IT engineers to spot trends in application usage which can be used to predict, and then prevent, congestion.
Application intelligence effectively allows you to create an early warning system for real-time vigilance. In the context of improving network security, application intelligence can provide the following benefits:
- Identify suspicious/unknown applications on the network
- Identify suspicious behavior by correlating connections with geography and known bad sites
- Identify prohibited applications that may be running on your network
- Proactively identify new user applications consuming network resources

A core feature of application intelligence is the ability to quickly identify ALL applications on a network. This allows you to know exactly what is or is not running on your network. The feature is often an eye opener for IT teams, and they are surprised to find out that there are actually applications on their network they knew nothing about. Another key feature is that all applications are identified by a signature. If the application is unknown, a signature can be developed to record its existence. These unknown application signatures should be the first step as part of IT threat detection procedures so that you can identify any hidden/unknown network applications and user types. The ATI Processor correlates applications with geography, and can identify compromised devices and malicious activities such as Command and Control (CNC) communications from malicious botnet activities.
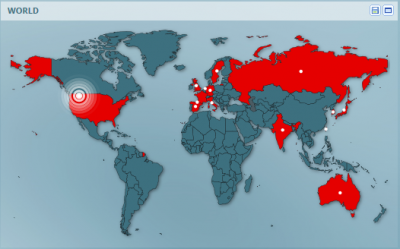
A second feature of application intelligence is the ability to visualize the application traffic on a world map for a quick view of traffic sources and destinations. This allows you to isolate specific application activity by granular geography (country, region, and even neighborhood). User information can then be correlated with this information to further identify and locate rogue traffic. For instance, maybe there is a user in North Korea that is hitting an FTP server in Dallas, TX and transferring files off network. If you have no authorized users in North Korea, this should be treated as highly suspicious. At this point, you can then implement your standard security protocols—e.g., kill the application session immediately, capture origin and destination information, capture file transfer information, etc.
Another way of using application intelligence is to audit your network policies and usage of those policies. For instance, maybe your official policy is for employees to use Outlook for email. All inbound email traffic is then passed through an anti-viral/malware scanner before any attachments are allowed entry into the network. With application intelligence, you would be able to tell if users are following this policy or whether some are using Google mail and downloading attachments directly through that service, which is bypassing your malware scanner. Not only would this be a violation of your policies, it presents a very real threat vector for malware to enter your network and commence its dirty work.
Ixia’s Application and Threat Intelligence (ATI) Processor brings intelligent functionality to the network packet broker landscape with its patent pending technology that dynamically identifies all applications running on a network. The Ixia ATI Processor is a 48 x 10GE interface card that can be used standalone in a compact 1 rack unit high chassis or within an Ixia Net Tool Optimizer (NTO) 7300 network packet broker (NPB) for a high port density option.
As new network security threats emerge, the ATI Processor helps IT improve their overall security with better intelligence for their existing security tools. To learn more, please visit the ATI Processor product page or contact us to see a demo!
Additional Resources:
- The Real Secret to Securing Your Network
- ATI Processor NetFlow Extensions Use the Splunk Enterprise Platform to Provide Customers with Greater Insight
- ATI Processor
- Ixia Net Tool Optimizer (NTO) 7300
Thanks to Ixia for the article.