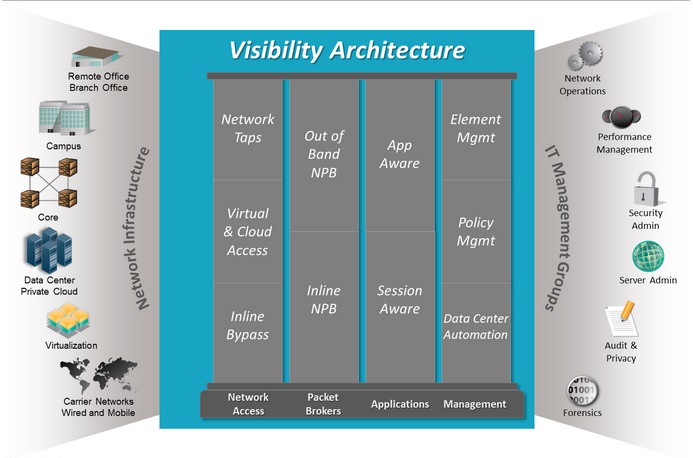
A Visibility Architecture, is an end-to-end approach to network, application, and security visibility. For some, the first questions asked will likely be “What is a Visibility Architecture?” and “Can it really help me?” The answer to both questions is a resounding yes!
First of all, what do we even mean by visibility? Visibility is defined by Webster as the “capability of being readily noticed” or “the degree of clearness.” By network or application visibility, for example, we are talking about the ability to readily see or quantify the performance of the network and/or the applications running over the network – usually by inspecting the packets traversing the network. Visibility in the network also reveals security vulnerabilities. This visibility is what enables IT to quickly isolate security threats and resolve performance issues, ultimately ensuring the best possible end user experience. Another way to think about this is that visibility IS what allows IT to control and optimize the network and the applications it services.
This is why network, application and security visibility are absolutely vital for any IT organization to accomplish their job! Without visibility, IT can only operate reactively to problems and will never be truly effective.
A Visibility Architecture is the end-to-end infrastructure which enables physical and virtual network, application, and security visibility. IT could piecemeal a Visibility Architecture together while fighting one fire after another as they occur, and still not have a cohesive strategy. This practice only leads to unnecessary complexity and far higher costs! With visibility so critical to IT’s primary objectives, a more strategic and proactive approach to building the Visibility Architecture makes total sense.
This is where a visibility architecture can help, since it is built for an enterprise’s current needs while also scaling and adapting to future needs. A Visibility Architecture addresses all three frameworks that make up a strategic end-to-end Visibility Architecture – network, virtual, and inline security visibility – yielding immediate benefits such as the following:
- Eliminating blind spots
- Controlling costs while maximizing ROI
- Simplifying control

First, a full array of access solutions for both physical and virtual deployments can be leveraged so that network operators don’t have to make compromises when it comes to visibility. This removes the bottle neck caused by limited access points (SPAN ports). It is also now possible to bring visibility to your virtual (or east-to-west) traffic within the virtualized data center without sacrificing the performance of host servers. And providing reliable access to inline security tools can improve security without compromising network integrity. This eliminates the blind spots in your network that are harboring potential application and security issues.
Enterprises can maximize their investment by using powerful network packet brokers (NPB). This gives greater control to network operators and enables the ability to extend the life of existing network, application, and security tools even as you migrate to higher speed 10GE, 40GE, or even 100GE networks. Filtering, aggregation, and load balancing capabilities, for example, ensure the tools get the data they need without being overwhelmed. This helps the tools provide trustworthy and actionable insight. The right NPBs allow you to pay for tool capacity only as your network needs grow, helping to minimize your costs.
Visibility does not have to get in the way of your business initiatives. A Visibility Architecture can seamlessly integrate into your existing network management and orchestration systems. It can also extend data center automation or application management. Advanced Visibility Architectures will take advantage of the power of automation. For example, your tools can now automatically, without manual intervention, request specific types of traffic when it detects a security issue. And if a tool goes down, load balancing can automatically compensate for this by sending traffic to the remaining tools until a replacement can be deployed.
So what does a successful Visibility Architecture look like? And what are the components that make up a full end-to-end visibility architecture? Read about it in Ixia’s latest White Paper here.