Ixia recently added passive SSL decryption to the ATI Processor (ATIP). ATIP is an optional module in several of our Net Tool Optimizer (NTO) packet brokers that delivers application-level insight into your network with details such as application ID, user location, and handset and browser type. ATIP gives you this information via an intuitive real-time dashboard, filtered application forwarding, and rich NetFlow/IPFIX.
Adding SSL decryption to ATIP was a logical enhancement, given the increasing use of SSL for both enterprise applications and malware transfer – both things that you need to see in order to monitor and understand what’s going on. For security, especially, it made a lot of sense for us to decrypt traffic so that a security tool can focus on what it does best (such as malware detection).
When we were starting our work on this feature, we looked around at existing solutions in the market to understand how we could deliver something better. After working with both customers and our security partners, we realized we could offer added value by making our decrypted output easier to use.
Many of our security partners can either deploy their systems inline (traffic must pass through the security device, which can selectively drop packets) or out-of-band (the security device monitors a copy of the traffic and sends alerts on suspicious traffic). Their flexible ability to deploy in either topology means they’re built to handle fully stateful TCP connections, with full TCP handshake, sequence numbers, and checksums. In fact, many will flag an error if they see something that looks wrong. It turns out that many passive SSL solutions out there produce output that isn’t fully stateful and can flag errors or require disabling of certain checks.
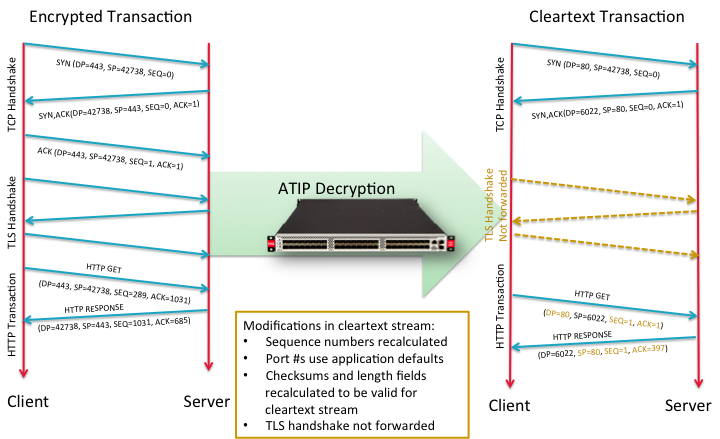
What exactly does this mean? Well, a secure web connection starts with a 3-way TCP handshake (see this Wikipedia article for more details), typically on port 443, and both sides choose a random starting sequence (SEQ) number. This is followed by an additional TLS handshake that kicks off encryption for the application, exchanging encryption parameters. After the encryption is nailed up, the actual application starts and the client and server exchange application data.
When decrypting and forwarding the connection, some of the information from the original encrypted connection either doesn’t make sense or must be modified. Some information, of course, must be retained. For example, if the security device is expecting a full TCP connection, then it expects a full TCP handshake at the beginning of the connection – otherwise packets are just appearing out of nowhere, which is typically seen as a bad thing by security devices.
Next, in the original encrypted connection, there’s a TLS handshake that won’t make any sense at all if you’re reading a cleartext connection (note that ATIP does forward metadata about the original encryption, such as key length and cipher, in its NetFlow/IPFIX reporting). So when you forward the cleartext stream, the TLS handshake should be omitted. However, if you simply drop the TLS handshake packets from the stream, then the SEQ numbers (which keep count of transmitted packets from each side) must be adjusted to compensate for their omission. And every TCP packet includes a checksum that must also be recalculated around the new decrypted packet contents.
If you open up the decrypted output from ATIP, you can see all of this adjustment has taken place. Here’s a PCAP of an encrypted Netflix connection that has been decrypted by ATIP:

You’ll see there are no out-of-sequence packets, and no indication of any dropped packets (from the TLS handshake) or invalid checksums. Also note that even though the encrypted connection was on port 443, this flow analysis shows a connection on port 80. Why? Because many analysis tools will expect encrypted traffic on port 443 and cleartext traffic on port 80. To make interoperability with these tools easier, ATIP lets you remap the cleartext output to the port of your choice (and a different output port for every encrypted input port). You might also note that Wireshark shows SEQ=0. That’s not the actual sequence number; Wireshark just displays a 0 for the first packet of any connection so you can use the displayed SEQ number to count packets.
The following ladder diagram might also help to make this clear:

To make Ixia’s SSL decryption even more useful, we’ve also added a few other new features. In the 1.2.1 release, we added support for Diffie Helman keys (previously, we only supported RSA keys), as well as Elliptic Curve ciphers. We’ve also added reporting of key encryption metadata in our NetFlow/IPFIX reporting:

As you can see, we’ve been busy working on our SSL solution, making sure we make it as useful, fast, and easy-to-use as possible. And there’s more great stuff on the way. So if you want to see new features, or want more information about our current products or features, just let us know and we’ll get on it.
More Information
Wikipedia Article: Transmission Control Protocol (TCP)
Wikipedia Article: Transport Layer Security (TLS)
Thanks to Ixia for the article.