Two common methods to copy traffic to your monitoring or security tools is a Span port or network tap. Span can be convenient for quick troubleshooting, remote locations or when you do not have access to the physical infrastructure. The risk of using a span port is that
- It can be over subscribed, and the lowest priority when it comes to forwarding all the packets to the intended device.
- Using a SPAN port is processor-intensive and can have a negative performance on the switch itself.
To avoid this we can use a network TAP which is a simple device that connects directly to the cabling infrastructure to split or copy packets for monitoring purposes such as security or packet capture devices.
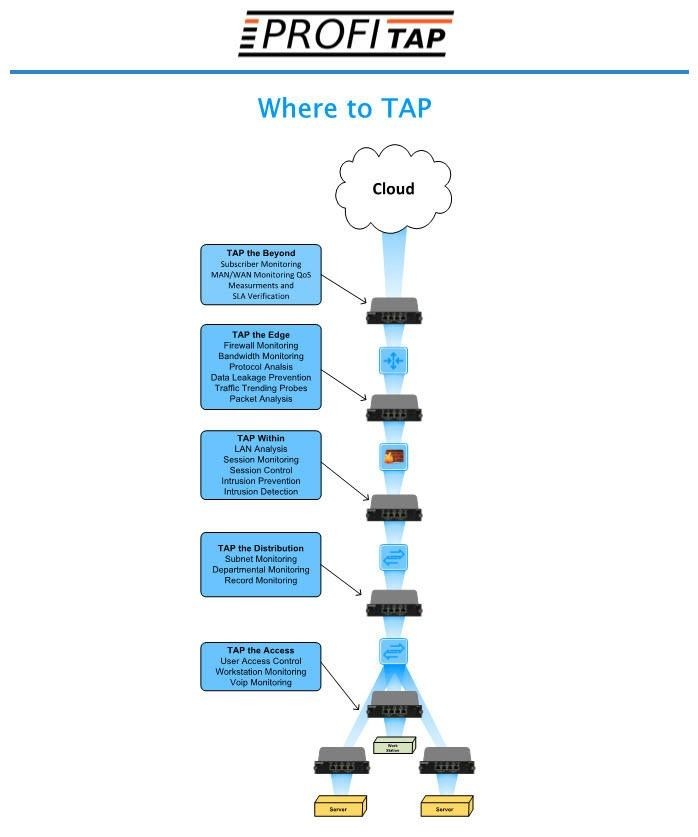
So where do I deploy a tap? A quick answer to this is anywhere you need 100% of the data all the time from L1 to L7. The above diagram is also a useful reference guide.
Thank you to ProfiTap for the article.