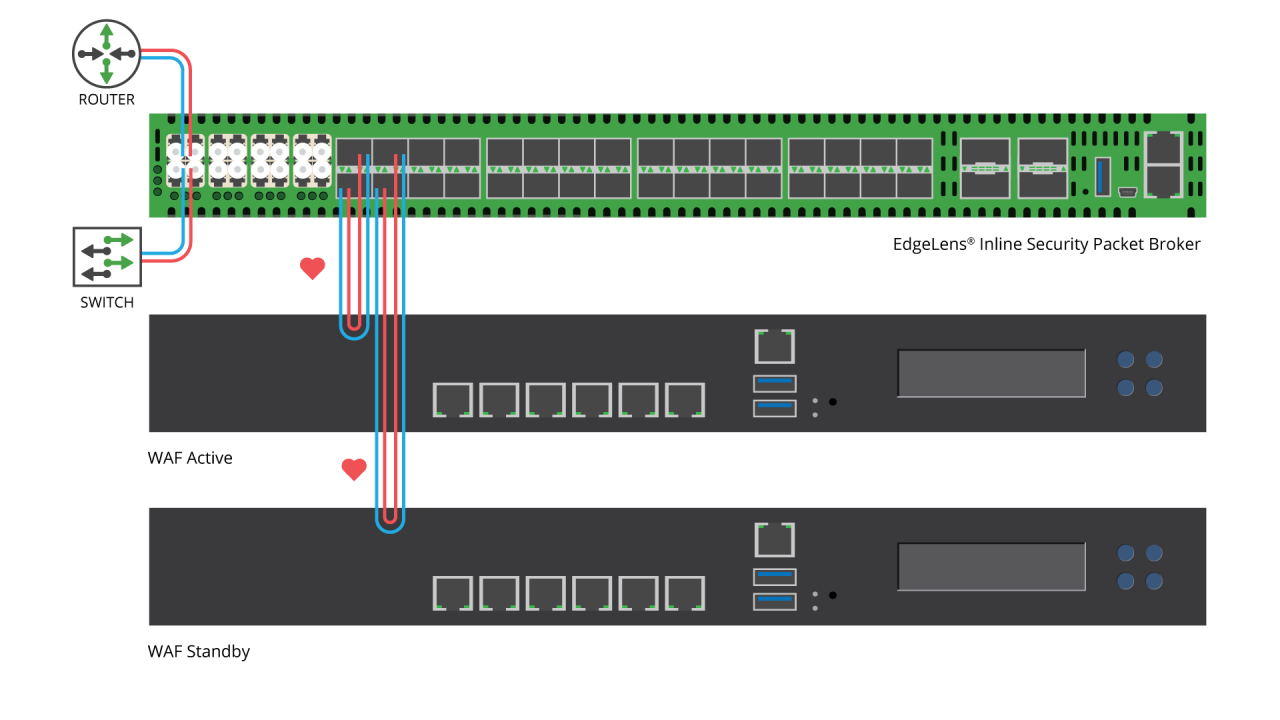
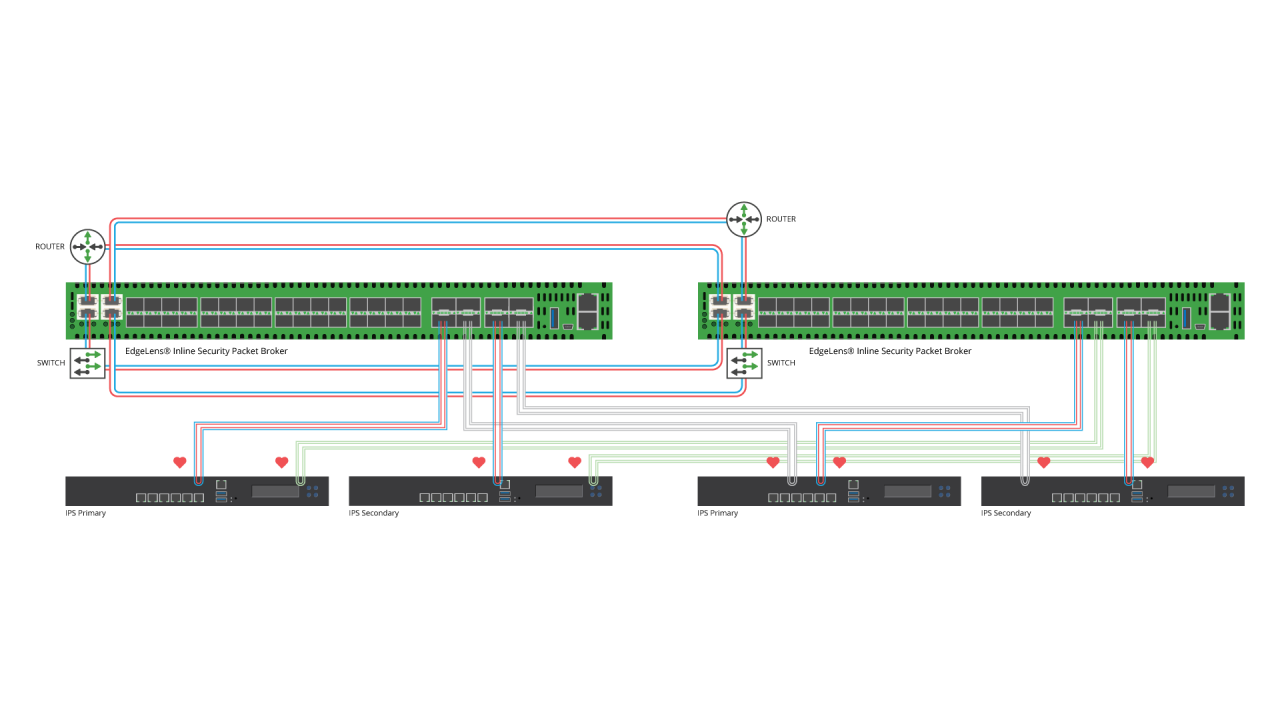
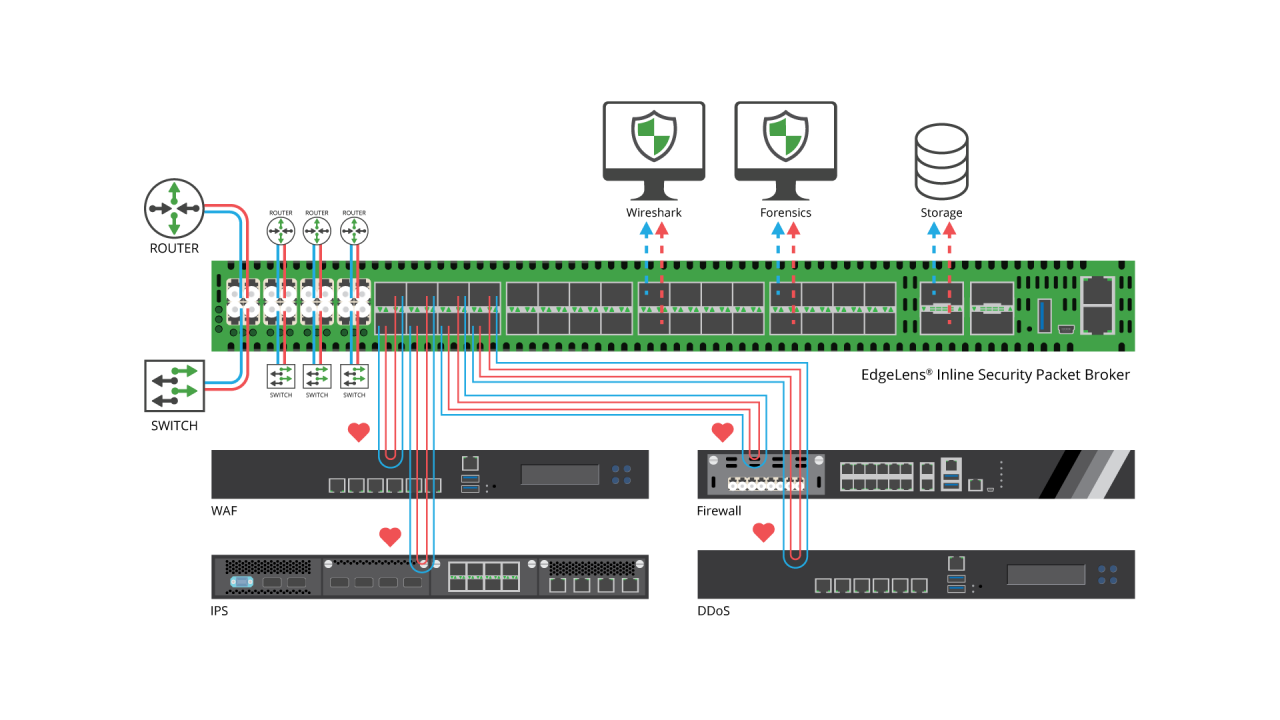
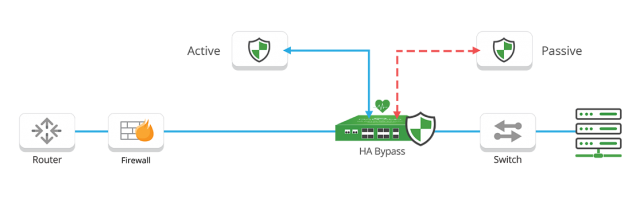
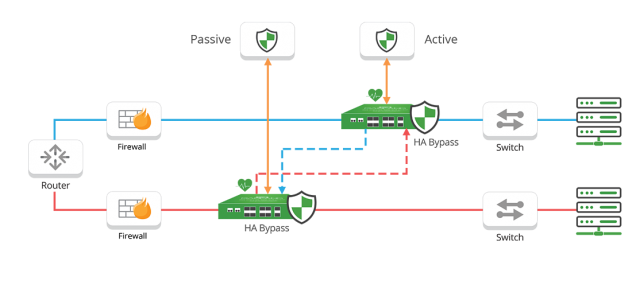
Network visibility solutions help organizations to meet their business and IT objectives by improving network performance, security posture, network planning, business continuity, and the ROI of network infrastructure and network tools. Network visibility products typically include network TAPs, Network Packet Brokers, Bypass Switches and Network Probes and the intelligence and advanced capabilities of a network visibility solution is mainly provided by the Network Packet Brokers (NPB).
NPBs are able to remove network traffic blind spots, optimize network traffic, filter network traffic, load balance, and support high speed connections (currently) up to 400Gbps. These capabilities increase the effectiveness of network monitoring, security and analytics network tools, reduce their loading, increase their availability and efficiency, and mitigate disparate network and tool speed and media connections. Network visibility has become fundamental for the successful outcome of contemporary IT initiatives including 5/4/3G service assurance, Digital Transformation, Data Security, Virtualization, Software Defined Networking and high performance, in order to remove the new, incremental network blind spots introduced by these initiatives as well as provide the benefits described above.
Any business case, of course, is dependant on the specifics of the benefits vs costs of a particular use case in a particular environment and organization. However, there are three typical areas of cost and operational benefits for deploying network visibility solutions that are useful to consider:
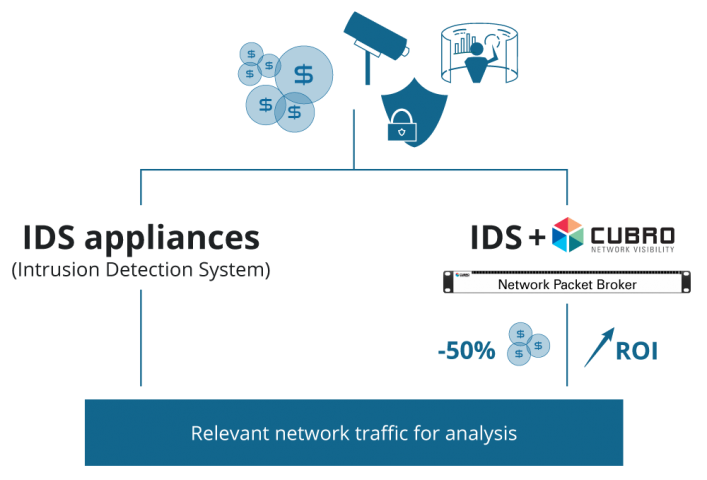
Reduction of the purchase cost and increase of Return on Investment (ROI) of network monitoring, security and analytics tools.
Reduce costs while improving IT services by reducing network downtime.
According to Gartner, the global average cost of downtime for businesses and organizations is $5,600 per minute, or over $300K per hour – taking into account the loss of revenue per working hour, the cost of restoring IT services, compensation and legal fees, and the cost of salaries of workers unable to work due to network downtime.
The overall average cost of downtime, of course, is a broad measure, but 98% of organizations confirmed that an hour of network downtime costs them over $100K, 81% of organizations confirmed that an hour of network downtime costs them over $300K, and 33% of organizations confirmed that an hour of network downtime costs them between $1M and $5M. These figures indicate that the larger an organization is the larger the cost and impact of network downtime is to them.
The average price of a network visibility solution to help reduce network downtime by removing network blind spots that can obscure network performance risks is in the range of $100k-$200K for Enterprises and $500k – $1M for Service Providers. As you can see, eliminating a single hour of average network downtime can potentially pay for the network visibility solution and deliver a very fast and high ROI.
Reduce costs while improving IT security by improving network security posture.
The IBM/Ponemon Cost of a Data Breach report for 2021 provides useful insights into the cost and nature of security breaches over the last year having studied 537 real breaches experienced by SMEs and larger enterprises across 17 countries/regions and 17 industries.
The average total cost of a security breach was $4.24M ( a 10% increase from $3.86M in 2020 ). The average cost was determined by including the cost for detection and isolation ( activities that enable an organization to reasonably detect the breach ); lost business ( activities that attempt to minimize the loss of customers, business disruption and revenue losses ); notification ( activities that enable the organization to notify data subjects, data protection regulators, and other third parties ); and post breach response ( activities to help victims of a breach communicate with the organization and redress activities to victims and regulators ). The largest contributor to the average data breach cost was lost business at an average cost of $1.59M.
The costs were further broken down into average cost for a data breach at a large enterprise ( > 10k employees ) was $5.5M, and for an SME ( < 500 employees ) was $2.98M ( up by 27% from $2.35M in 2020 ), with an average cost per stolen record of $161 ( up by 10% from $146 in 2020 ).
Once again, deploying a network visibility solution to remove network blind spots that obscure network security risks and improve network security posture can enjoy a very fast and high ROI by eliminating a single average data breach.
As new ‘blind spot’ generating IT initiatives are deployed and the ongoing risk and cost of network security breaches continues to increase, network visibility solutions have become critical components for networks to successfully support businesses and organizations. Network visibility solutions, such as those from Cubro that provide the best ‘features to price’ ratio in the market, deliver advanced capabilities to help improve network performance, availability and security posture while reducing capex and opex costs and increasing ROI, and are an essential and affordable investment.