Network visibility is a crucial aspect to improving network security and optimizing network monitoring capabilities. At the same time, it is an evolving technology. In this blog, I’m using some interesting data that Enterprise Management Associates (EMA) captured in a survey they conducted for Ixia in late 2016. This data is great because it allows you to see what’s changed over the last several years and how others are using technology to improve their networks.
For instance, are you monitoring 100% of your network? Most, 60%, of enterprises are not able to do this. This is in spite of the fact that IT has been deploying lots of security and monitoring tools in the last several years.
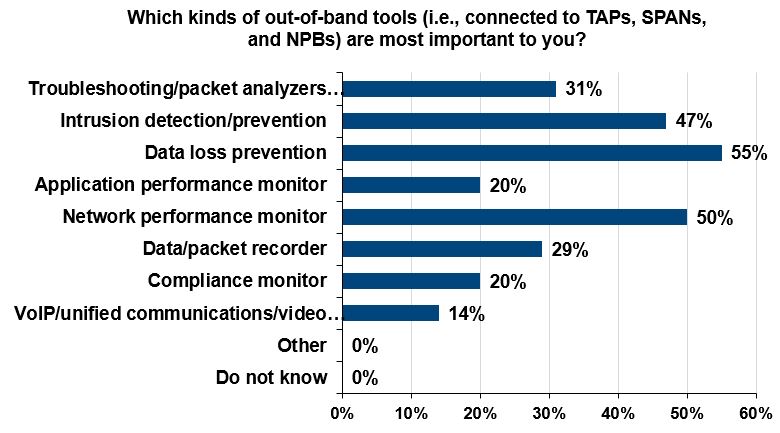
So what kind of security and monitoring tools are people deploying, you might ask? According to the survey, the most common out-of-band tools (i.e. tools not connected directly in the path of live traffic) are: data loss prevention (DLP), network performance monitoring (NPM), and intrusion detection systems (IDS).
There is also a significant expansion of taps being installed into the network while SPAN usage is decreasing. In 2009, 21% of respondents relied solely on SPANs for data access. As of 2016, that number is now 1%, as you can see in the following chart.
This means that a 100% SPAN approach for access to monitoring data is history. In fact, for 78% of businesses, more than half of their monitoring data access is now based upon tap technology.
Unfortunately, there is still a lot of data access reconfiguration required to get the proper data to monitoring tools. In fact, 49% of respondents changed the locations from where they mirror traffic to their network security and monitoring tools more than 3 times per month. This is a lot of wasted effort and money.
Another interesting response showed that while 40 Gbps links are now mainstream, only 1/3 of the respondents use 40 Gbps tools on their networks. The rest use lower rate (like 10 Gbps) tools or they don’t monitor those segments at all.
Furthermore, according to the survey, the most important monitoring features to IT staff for an NPB are: data filtering, SSL decryption, and high availability.
Thanks to Ixiacom.com and author Keith Bromley for this article.