
Accelerate Innovation to Connect and Secure the World
Keysight is your innovation partner for Network Visibility, Security and Test Solutions.
Delivering market-leading design, emulation, and test environments that help you develop and deploy faster, with less risk, throughout the product life cycle.
Solutions
Keysight Technologies offers comprehensive network visibility, testing, and security solutions that empower organizations to monitor, analyze, and secure their networks effectively.
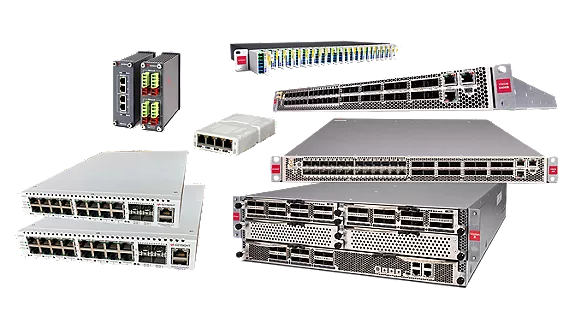
Network Visibility
Better visibility into physical, virtual and software defined networks with network packet brokers, bypass switches and network taps
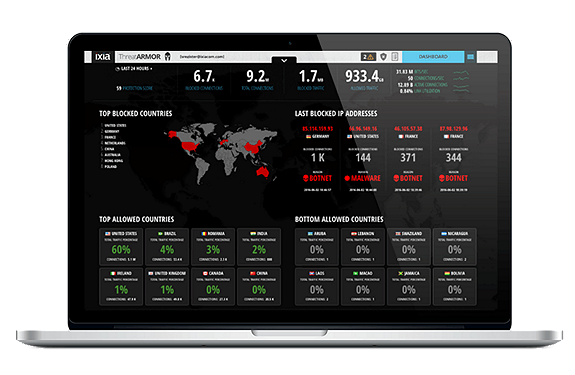
Network Test & Security
Ensuring high performance of wired, Wi-Fi, and 3G/4G/LTE and 5G networks in both pre-deployment and real-world environments while enabling dynamic security intelligence to help stay one step ahead of attacks
Network Visibility For Hybrid Networks
Keysight can help. Customers rely on Keysight’s network visibility solutions to deliver rich data about network traffic, applications, and users across any networking environment. These deep insights are what Keysight calls dynamic network intelligence. It helps your organization continuously innovate, meet aggressive service level agreements, adhere to compliance regulations and keep applications running smoothly and securely.
Network Packet Brokers

- Dedicated hardware acceleration provides a Zero packet loss architecture
- Filtering of traffic so that each monitoring or inline security tool receives exactly the right data
- SSL decryption to quickly detect emerging threats encrypting exploits within application traffic
- Dynamic filter compiler handles all filter rule complexities automatically – no overlapping filter rule headaches
- Aggregation of traffic from multiple TAPs or SPAN ports
- Load-balancing of traffic to multiple analysis tools
- L7 application awareness efficiently allows for packet processing based on unique applications
Network TAPs
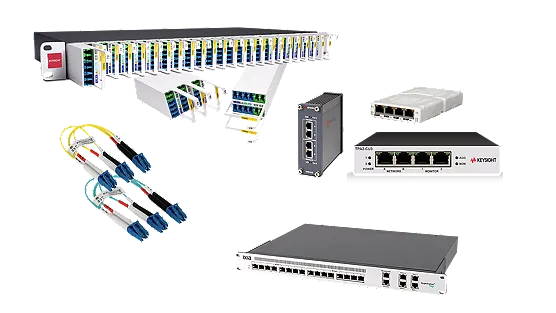
- Provide 100% visibility to link traffic to security and network monitoring tools
- Save valuable rack real estate with high-density tap, aggregator, and regenerator solutions
- Realize very low acquisition cost with minimal cost of ownership
- Eliminate high costs and potential blind spots associated with adding SPAN ports
- Deliver fully passive functionality so monitoring infrastructure does not impact network availability
Other Keysight Visibility Products
Network Packet Brokers
Keysight’s best-in-class network packet brokers, deliver inline or out of band operation without packet loss, using filters and active-active security.
Bypass Switches
Bypass switches (formerly NetOptics) provide automated fail-safe, in line protection for any size active-active or active-passive networks.
Network Taps
Network tap products – optical fiber taps, copper taps, aggregators, regen taps – provide visibility into network traffic, performance and security.
Aggregators
Keysight’s iLink Aggregators are cost effective solutions for the tapping and aggregating of traffic to feed to network monitoring or cyber security tools.
Cloud Visibility
Migrate to the cloud with complete visibility across public, private, and hybrid environments.
Performance Monitoring
Network performance monitoring solutions offer proactive performance monitoring and real world simulations for confidence in network performance.
Vision Edge OS
Vision Edge OS software offers complete access for real-time visibility, insight, and security into high density hyperscale/microscale and SDDC networks.
Keysight Vision Orchestrator
Keysight Vision Orchestrator eases your ability to manage, configure and monitor the devices in your network.
Clock Synchronization
Trusted by the world’s largest enterprise organizations, TimeKeeper® is the most accurate, reliable and verifiable time-sync solution available.
Fabric Controller
Fabric Controller provides software software defined visibility (SDV) for physical, virtual and SDN networks.
Find Your Visibility Platform

NetStack
Robust filtering, aggregation, replication and more — the gold standard for visibility

PacketStack
Intelligent packet filtering, manipulation and transport

SecureStack
Optimized handling for secure traffic

AppStack
Context aware, signature based application layer filtering

MobileStack
Visibility intelligence tailored for the mobile carrier evolved 5G packet core
Ready to Drive Your Organization Forward?
To request a technology demo or a quote, reach out to the experienced and knowledgable Telnet Networks Sales and Engineering team. We're looking forward to partnering with you.
Network Test and Security
Ensuring high performance of wired, Wi-Fi, and 3G/4G/LTE and 5G networks in both pre-deployment and real-world environments while enabling dynamic security intelligence to help stay one step ahead of attacks
Protocol and Load Test
Test and validate your device, network, and service performance at scale
Test Hardware
Enterprise-wide application and security testing from anywhere, anytime
Network Security Suite Products
Application and Threat Intelligence
Keysight’s ATI team works 24/7 to deliver continuous real-time data feeds to assure that you always have the most current application and threat intelligence.
