Network Testing & Emulation Solutions
Market leading network testing software (LANforge) and traffic emulation equipment and solutions for WiFi and Ethernet networks
Traffic Generation & Emulation Platforms
All LANforge systems include a platform independent Graphical Management Client with virtual network configuration reporting, test management and automation capabilities.
LANforge-FIRE & LANforge-WiFIRE
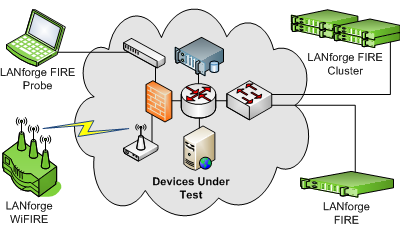
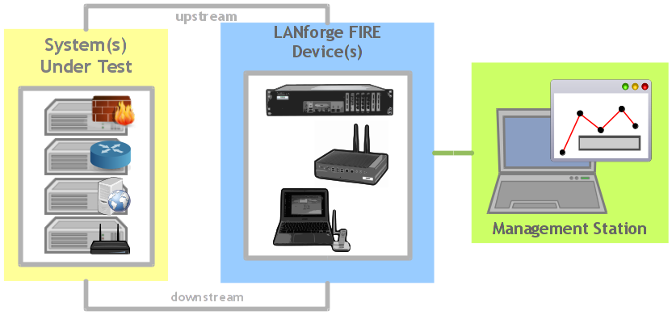
LANforge-FIRE and LANforge-WiFIRE generate stateful network traffic at various speeds with the ability to monitor packets for throughput and correctness. LANforge-FIRE sits on the edge of your network and tests your network core. WiFIRE systems can emulate up to 200 wireless client stations (Virtual STAs) per radio.
LANforge-ICE
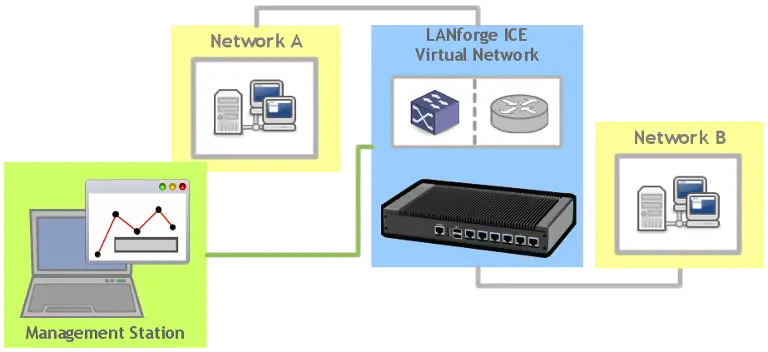
LANforge-ICE emulates networks by connecting virtual routers and other virtual network elements. LANforge supports many impairments: latency, bandwidth, jitter, packet loss, packet reordering, corruption and more. LANforge ICE tests the behaviour of devices that sit on either side of an impaired network.
Use Cases
WiFi Traffic Generation
Test and validate WiFi Access Points and deployments. Test multi protocol, high density and authentication models. Traffic generation features include HTTP, TCP, UDP, TCPv6, UDPv6, SIP and RTP. Support for Wifi 1 through 7.
Stateful Traffic Generation
Create load on a network under test. Report statistics such as packets sent and received, latency, packet-loss and many other network characteristics. LANforge stateful TCP connections and can also act as group of routers. Virtualize network adapters and wifi station interfaces.
WAN/Network Impairment
Verify applications can run over a WAN Test LAN based applications for adverse network conditions. Typical impairments would be delay (latency), bandwidth constraint, jitter and packet loss. Corruptions, packet reordering and complete link loss can also be applied.
Network Simulation
Simulate large complicated networks. LANforge supports virtual routers, switches, multi-hop networks and more. Protocols supported include spanning-tree for switches and OSPF, BGP, RIP, IGMP, an PIM (Multicast) for routers
VoIP/RTP Call Generation
LANForge can be used to load SIP gateways and other VOIP infrastructure. It can report various statistics, including PESQ quality scores. Can be used in Gateway or direct mode with support for SIP authentication and for multiple Codecs.
LANforge-FIRE
Generates stateful network traffic at various speeds with the ability to monitor packets for throughput and correctness. LANforge-FIRE sits on the edge of your network and tests your network core.
LANforge-ICE
Emulates networks by connecting virtual routers and other virtual network elements with links that alter bandwidth, latency, packet loss and corruption. LANforge ICE tests the behaviour of devices that sit on either side of an impaired network.