Passive fiber optic taps are very simple devices. They almost never go wrong. In fact they have MTBF figures calculated in millions of hours. You will certainly die before they will! However Ixia often gets questions from customers of the kind “I’ve installed your tap, but it does not work – please send me a new one”. In almost all cases this is due to incorrect installation of the tap. In this blog I’ll cover one example of a common error and how to avoid it, but look out for some more blogs on this topic going forward.
1G and 10G Fiber optic TAPs such as Ixia’s Flex TAP have two LC outputs that correspond to traffic flowing through the tap in two directions. 1G/10G Fiber optic links have a duplex pair of fibers and the two outputs correspond to the traffic flowing through the TAP. These are called Left and Right traffic, or DCE and DTE traffic. These two outputs have to be fed to two monitoring ports and two transceivers have to be used to receive the traffic as only the receive side of the transceivers can be used. This creates a challenge as the output from the fiber TAP is a duplex connector and yet two separate connectors are needed to connect to two different transceivers. There are three alternatives:
- Use 2 separate simplex cables.
- Use a duplex cable and with a sharp knife split the two ends apart.
- Use a specialist Y cable
The first two options have a pitfall that sometimes traps operational staff in data centers. The TAP will only work if the cable from the TAP is fed into the receive side of the transceiver. As operational staff are used to usually working with duplex cable and dual fiber transceivers they may not know (or simply make a mistake) and connect to the transmit side of the transceiver in error. In this case not only will the TAP appear not to function, but if the analytic tool is set to allow traffic to be generated on these transceivers, traffic could be injected back into the TAP.
In this scenario a user may think the TAP is not working, when in fact its just been connected up incorrectly.
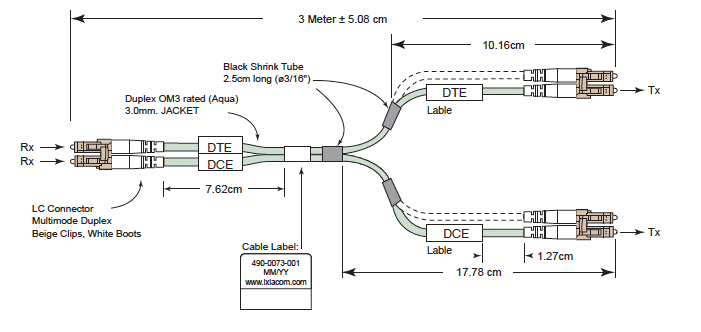
To avoid this problem its best to use a specialist Y cable that converts a duplex connector to two duplex connectors that are orientated so the light is only fed into the receive side of the transceivers – easier to explain with a diagram! See below for a diagram of an Ixia Y cable for use with its Flex TAP passive fiber TAPs:-
This shows a Y cable that Ixia sells to complement its range of Flex TAPs. As you can see the Y cable is constructed in such a way that the light from the TAP (which is connected on the left hand side of the above diagram) is fed correctly to the two receive ports of the transceivers (which would be on the right hand side). Yes, Ixia makes money out of these, but they are relatively low cost (a list price of less than $100 ea. and they also include two network side cables) and the one time a TAP is connected to the wrong side of a transceiver and hours have to be spent figuring out what is wrong, is the time you come to realize that “Y Cables Matter”.