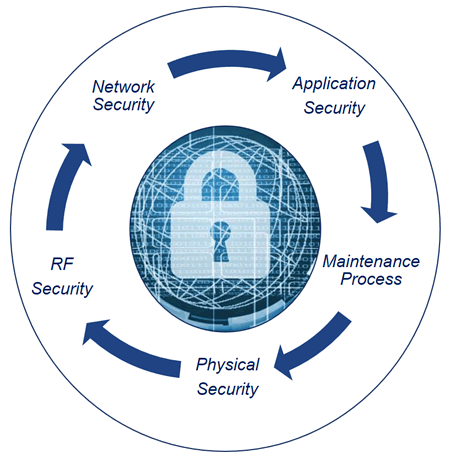
For a resilient positioning, navigation and timing (PNT) solution you need to build layers of defense, which includes physical security to RF security, network security, application security and ongoing maintenance/support.
How Orolia Provides Resilient PNT Cybersecurity
Physical Security
- The simplest Denial of Service attack is to merely disconnect the power on the equipment by turning it off or pressing a few buttons to disable operation. So, the first step in cybersecurity is always Physical Security – protect the equipment from unauthorized or accidental manipulation.
- But we take Physical Security a step further by designing our equipment to be robust and protected from inadvertent defeat. Our SecureSync® time servers offer fully independent, redundant power inputs (A and B side) so that our customers can secure the power entry to ensure that a single power failure will not deny operation.
- Our products include the ability to lock the front panel access controls, so that even personnel who have physical access to the rack cannot change settings unless authorized.
- We are ISO 9001:2015 certified – your guarantee that stringent manufacturing and quality controls are in place.
RF GNSS Security
- We offer BroadShield™ interference and spoofing detection on received GPS signals and ThreatBlocker in-line anti-jamming and spoofing protection.
- Our 8230AJ GPS/GNSS Anti-Jam Outdoor Antenna offers horizon blocking technology to protect against intentional or unintentional jamming or spoofing.
- With alternate signal solutions such as STL augmentation, you can receive precise time and position information even in GPS-denied environments, and you can authenticate GPS to prevent spoofing by using an encrypted signal.
- The GPSdome Anti-Jammer is the industry’s only non-ITAR GPS anti-jammer and provides protection against GPS jamming, ensuring continuity of autonomous navigation and operation during jamming conditions.
Orolia’s resilient PNT network solutions help protect against cyberattacks with the following features:
- Access control lists (ACL) limit network access to only authorized users.
- We provide the ability to disable services and ports – admin level configuration to enable only those services and ports that are necessary for operation.
- User data is not stored on our time servers – though they are servers in the general sense, they are outputting precise time, not serving a file storage function (other than activity logs), so there is no user data to be compromised.
- Iptables: We support iptables in our time servers. With Iptables, customers can create their own set of security rules using the source and destination of the IP address and/or port numbers. Using iptables, customers can add such alternative layers of security rules to prevent unauthorized and unwanted access to the system.
- Our SecureSync time servers are approved for use by US federal defense agencies, including DISA. SecureSync is the first and longest-standing DISA-approved time server.
Orolia’s Resilient PNT applications include built-in security such as:
- AAA – Authentication, Authorization and Accounting– Our products adhere to AAA security practices. The following protocols are supported:
- LDAP
- RADIUS authentication
- TACACS+ (Cisco)
- Multi-level authorization
- Configurable, complex passwords that expire periodically and cannot be reused
- HTTPS — no-clear text is standard, using signed certificates (SHA256 default) with configurable cipher usage and TLS v1.1 and v1.2
- NTP – symmetric keys and autokey. Orolia also serves on the standards setting committees for the creation of more robust protocols.
- SSL, SSH, SCP, SFTP with public/private key support
- Compliance with NIST standards for Personally Identifiable Information and Digital Identity Guidelines
We scan continuously against CVEs (Common Vulnerabilities and Exposures), and issue routine software update releases with safeguard protections.
How to Defend Against Cyberattacks that Affect PNT Data
While no solution can fully guarantee your protection against cyberattacks that affect PNT data, there are a few simple steps you can take to protect yourself against the most common threats.
- Use only Resilient PNT solutions that offer comprehensive layers of defense, such as those provided by Orolia.
- Have jamming and spoofing protection in place, such as BroadShield, Orolia’s 8230AJ GPS/GNSS Anti-Jam Outdoor Antenna, or the GPSdome Anti-Jammer.
- Always ensure that you have the latest Resilient PNT software updates with a complete maintenance plan. Update Your SecureSync Software Now
Keys to Security: The AAAs
Authentication — you are who you say you are
Authorization — you have proper permission
Accounting — traceable actions – you know if you have been hacked
Guide to Basic Cybersecurity
RMF – Risk Management Framework – https://www.corsec.com/rmf/
- Umbrella process for all cybersecurity defined by the US DoD
- STIGs – Secure Technical Information Guide – subject specific specifications under this framework
- Replacement for the old DIACAP
Certifications
- DoDIN APL – DoD Information Network Approved Products List
- FIPS 140-2 – US Fed standard for encryption devices and those connecting to classified nets
- Common Criteria – ISO 15408 – EAL levels 1-7; targeting level 3 – Methodically Tested
- NIAP – National Information Assurance Partnership – USA body responsible for CC cert
Other
- CVE – Linux Common Vulnerabilities and Exposures
- TACACS+ (Cisco) and Radius server AAA
- EAP/TLS – 802.1x E – Extensible Authentication Protocol / Transport Layer Security
- DoD PKI (Public Key Infrastructure) support
For more information on cybersecurity standards, refer to the following resources:
DISA RMF site
NIST RMF site
BSI Consulting RMF site
Gossamer Labs
NIST 800-53
NIST-800-37
NIST 800-122 Personally Identifiable Information
NIST 800-63 – Digital Identity guidelines
CEA Tech Cybersecurity
Tenable / Nessus
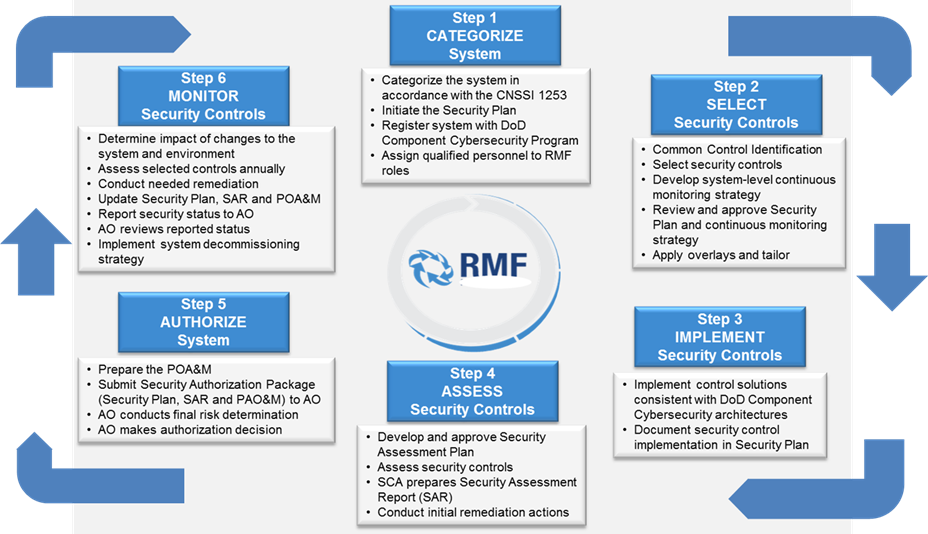
6 Steps to Protecting Your System
Resources

Resilient PNT: How to Detect, Protect and Prevent Disruption of GPS/GNSS/PNT Signals and Sources
Author David Sohn
David Sohn is a Solution Architect at Orolia, designing and developing solutions leveraging the organization’s precision timing solution portfolio, including their flagship SecureSync and VersaSync products, and contributing to its entire portfolio of resilient PNT solutions. He has more than 10 years of experience designing, developing, and managing precision timing solutions and holds a BS in computer engineering from The Pennsylvania State University.