Security is nowadays an important part of network management. Secure networks are vital for running an uninterrupted business, preventing data loss and maintaining the overall image of the business. Security challenges are increasing because networking is getting more complex, more dynamic and virtual.
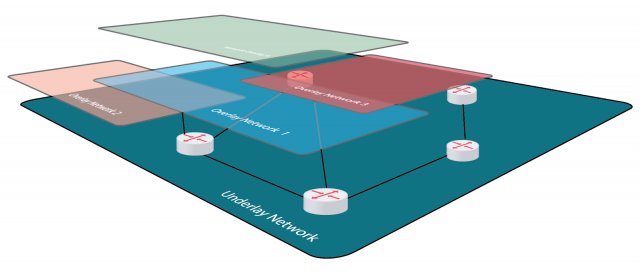
The existing approach of network visibility like in legacy times to tap a link and feed this to a tool is no longer valid. This approach is not appropriate because this “link” is not a physical link anymore. It is a virtual link on top of the physical network. The reason is that today more and more networks are designed as overlays.
These overlay networks are actually the operating network which should be monitored but a network TAP and a classical network packet broker (NPB) is a physical device which works on one layer below the overlay.
This would not be such a problem in theory if we expect to have only one overlay technology but in reality, overlay technologies are stacked and there are different overlays on the same physical network. In some cases, dozens or even hundreds of overlays are seen in large networks.
Based on this situation we have several challenges to tackle:
1. Current tools do not support these kinds of networks. If these tools are used, then it is necessary to separate these logical overlay networks and feed only the correct network to the tools.
- To do this, advanced NPBs are needed, which can filter in these virtual overlay networks.
- These virtual networks are more dynamic and are often triggered by the network itself, and unknown to the user because they are fully transparent to the overlay. “This is an advantage for usage, but a disadvantage for monitoring.”
2. Typically, such networks have more links to tap and often these links are 100 Gbit but the load is much higher. To deal with this issue, you need an NPB with features like smart filtering and steering in multiple 100 Gbit line speed. The solution to aggregate this traffic to a “smart device” and handle the traffic there will lead to other issues like:
- overload, over subscription and loss of packets
- extreme complex aggregation and dis-aggregation configurations
- adding additional delay
- cost
Thank you to Cubro for the article.