Solution Strengths
- comprehensive solution for Configuration, Performance and Fault Management
- unified code base eliminates need for fault prone module/product integration
- ultra scalable architecture, nothing gets added that could impact scalability
- End-to-End awareness delivers automated dependencies, root cause and
- delivers massive automation benefits
- ROI in months, not years
A truly ‘‘VendorAgnostic“ Solution
- supports many different network hardware manufacturers, including Cisco, Huawei, Juniper, Ixia, Junisphere, HP, Redback, Enterasys, Alcatel, RAD, and Foundry
- powerful device interaction scripting engine allows rapid support for new manufacturers or device models without development delays or major upgrades
- delivers the same level of functionality for all devices regardless of manufacturer
Why do we need NCCM?
- a recent Gartner study projected that “Through 2015, 80% of outages impacting mission-critical services will be caused by people and process issues, and more than 40% of those outages will be caused by change/configuration/release integration and hand-off issues.” (Ronni J. Colville and George Spafford Configuration Management for Virtual and Cloud Infrastructures)
- Enterprise Management Association reports that 60% of availability and performance issues/errors are the result of misconfigurations
- without a comprehensive plan to automate the repetitive and error prone “day to day” tasks, most organizations will face downtime and service failures due to something that could have been prevented
The StableNet® NCCM and VLM Framework
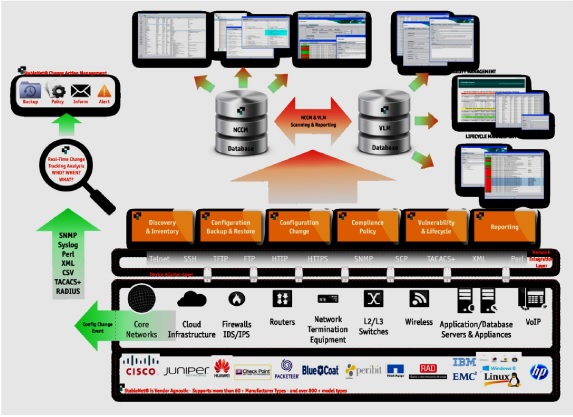
Best Practice #1 – Auto-Discovery Configuration Backup
- when discovering the network infrastructure hardware components it is essential that the software IOS image, along with the startup and running configuration files, are backed up as part of the initial discovery process
- having the ability to perform configuration backup is a fundamental requirement of any NCCM system however, having the flexibility to perform additional ‘show’ type commands as part of the configuration backup process to capture current snapshot states of the operating device is of huge benefit as additional device and operational performance data can also be collected and tracked at the same time
- StableNet® has this capability built into its NCCM module and so can subsequently track and report against previous and current operational states
Best Practice #2 – Automated Alerting
- it is essential to know when your infrastructure has been backed-up successfully, or if backups have failed, and more importantly why they have failed
- StableNet® has the capability to send notification updates of backup configuration job successes, failures, and why the job failed notifications can be emailed to targeted audiences, alerted via SMS (providing an SMS gateway is available), and via the Web & GUI clients
- having up-to-date and current device configuration of your infrastructure is paramount in the mitigation of potential catastrophic failure as it is a key component for the restoration of failed, or misconfigured, infrastructure
Best Practice #3 – Configuration Backup Scheduling
- once an infrastructure has been discovered and the configuration of that infrastructure estate is backed-up and being operationally managed, then you should look to employ a best practice backup schedule
- it is important to plan a backup schedule for implementation from day 1, and then fine-tune the schedule through the knowledge of the change analytics overtime
- most devices can also send syslog or traps when the configuration is changed, and this event can then automatically trigger a backup process to be initiated
The NCCM –Policy Compliance and Governance Structure
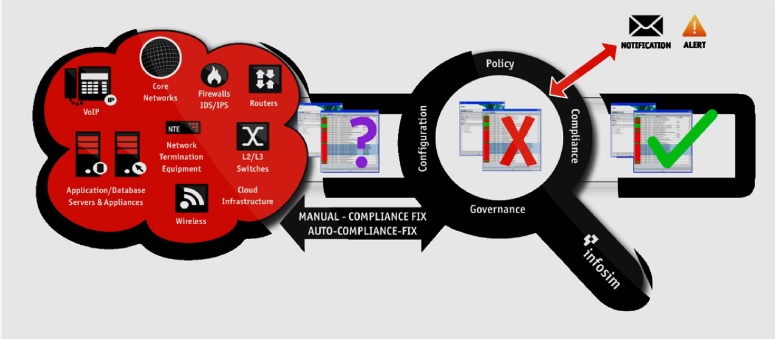
Policy Compliance
- many organizations today have configuration and security policy rules that require compliance checking to ensure consistency with design standards, processes and directives with internal and external regulators
- using manual processes is not recommended, as it is time-intensive, costly, inaccurate and more importantly, your business could be at risk and open to potential attacks through not having the desired real-time visibility
- the policy compliance and governance engine within the NCCM module of StableNet® allows corporations to create policies electronically in order to scan/analyze configurations of the infrastructure environment so as to produce accurate and timely compliance and violation reporting analytics
- whether you need to meet PCI, ITIL, FCAPS, ISO27001, SOX, NSA Security Guidelines or other business continuity or regulatory standards StableNet® can help greatly with simplifying the process, drastically reduce your risk, and drive compliance consistency throughout your infrastructure ensuring sustained levels of service availability
Best Practice #4 – Regulatory Compliance Policy
- governments and industry regulators require organizations to conform to standard best practices in order to become compliant with these regulations such as PCI, ISO27001, FCAPS, ITIL, SOX, HIPPA, and others, device configuration should conform to these standards
- StableNet® assists greatly with this regulatory requirement automatically checking for compliance to the rules defined reports on policy compliance and violations are available out-of-the-box
Best Practice #5 – Vendor Default Policies
- vendors ship devices with default configuration enabled to assist with out-of-the box implementation
- the default configuration settings are overlooked a lot of the time when the device in question is installed within the organizations infrastructure common settings, for example around default username and passwords, or SNMP ‘public’ and ‘private’ community strings etc. are not removed, leaving a hole in your security for potential access to attacks
- therefore, it is a best practice recommendation that you create policies to scan the configurations of your infrastructure devices to eradicate these potential holes in order that the risk can be mitigated and infrastructure security access is maintained to the highest possible levels
Best Practice #6 – Security Access Policy
- access to infrastructure devices are policed and controlled with the use of AAA (Authentication, Authorization, Accounting) TACACS+, RADIUS servers, and ACLs (Access Control Lists) so as to increase security access into device operating systems
- it is very important therefore that the configuration elements of infrastructure devices have the consistency across the managed estate it is highly recommended to create security policies so that the configurations of security access can be policed for consistency and reported on if changed, or vital elements of the configuration are missing
- StableNet® has the flexibility in-built to create these policy types and maintain the consistency required – this is also an NSA guideline requirement
Best Practice #7 – Service Design Rules Policy
- Telco’s, ISPs/MSPs and Enterprise organizations have service types that maybe predefined i.e. Standard, Enhanced and Premium service types
- creating design policy rules provides greater control around the service offerings, i.e. QOS settings for Enhanced service offerings, or a complete End-to-End service type, and ensures compliancy with the service delivery SLAs (Service Level Agreements)
- StableNet® allows for the creation of design policing of your entire service portfolio giving you that peace of mind that your services are being provisioned and assured in the way they were designed
The NCCM –Configuration Change Management
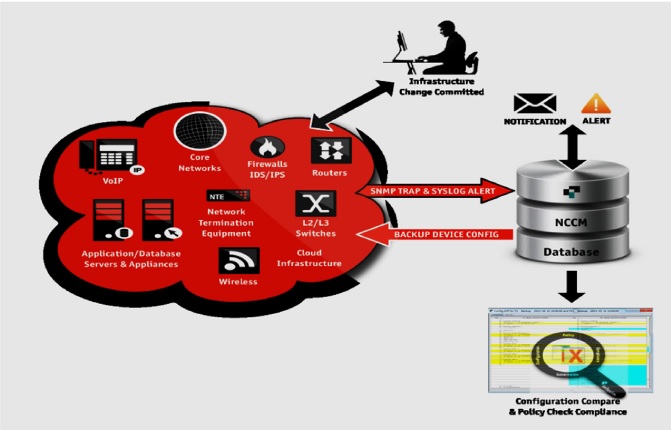
Best Practice #8 – Enabling of Real-Time Configuration Change Detection
- configuration compliance policy for SNMP and Syslog is essential for the assurance of receiving notifications of changes to device configuration unauthorized configuration changes are common practice within all sizes of business and so it is extremely important to have the necessary controls in place to notify and mitigate when a change was committed
Best Practice #9 – Configuration Change Compare Management
-
-
- having visibility of changes to the network infrastructure is essential for any NCCM implementation however, being able to compare configurations from previous known states is a powerful and quick way of identifying exactly what has changed, or been added, to a device configuration
- StableNet® has this capability built into its NCCM module and so can subsequently track and report against previous and current operational states
-
Best Practice #10 – Bulk Configuration Change
-
-
- automation is the important task in IT operations nowadays IT Managers are always looking for automating repetitive and time consuming tasks in order to reduce operational cost and improve productivity
- StableNet® NCCM supports you in this task by automating bulk configuration and change management for network devices tasks can be scheduled and configuration changes can be executed for individual or groups of network devices it is possible to alert on configuration change or policy failures and restore a known good configuration as required
-
The NCCM – Vulnerability Management
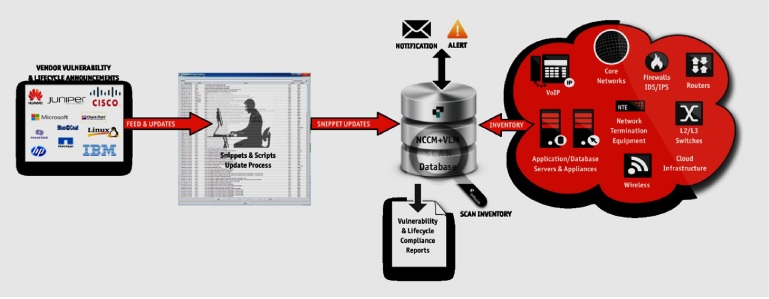
Best Practice #11 – Testing of New Vulnerabilities
-
-
- when vulnerabilities are announced by vendors it is advisable to perform test checks within a lab or incubation environment to identify any false positives, false negatives, and potential service disruptions by performing this testing and eradicating any potential errors the results on your live database will result in greater accuracy and compliance across your infrastructure
-
Best Practice #12 – Maintaining Vulnerability Optimization
-
-
- it is essential to Plan, Maintain, Optimize and focus on upholding accurate vendor updates
- having a process in place whereby announcements are captured and applied to your existing vulnerabilities data is paramount in maintaining a highly optimized vulnerability management system
- it is also important to note that once a vulnerability has been eradicated, or fixed, within your infrastructure you can not simply forget about it
- a vulnerability you thought was secure could be re-introduced at any time via a new device being installed, or an off-net device being re-introduced to the infrastructure hence its good policy and practice to run daily scans and updates
-
Best Practice #13 – Testing of New Lifecycle Announcements
-
-
- when EOS (End-of-Sale), EOL (End-of-Life), EOSS (End-of-Service-Support) lifecycle announcements are released by vendors it is advisable to perform test checks within a lab or incubation environment first to identify any false positives, false negatives, and potential service disruptions
- by performing this testing and eradicating any potential errors the results on your live database will result in greater accuracy and compliance across your infrastructure
-
Thanks to Infosim for the article.





