In our first post, we demystified the core philosophy of Zero Trust—shifting from the outdated “castle-and-moat” perimeter to a model that assumes a breach has already occurred. But once you’ve embraced the mindset of Never Trust, Always Verify, a practical question emerges: How do you verify what you cannot see?
At Telnet Networks, we break Zero Trust down into three actionable pillars: Enable, Protect, and Recover. Today, we’re diving into the first and most critical foundation: Pillar #1 – Enable.
The “Enable” Pillar: Fueling the Trust Engine
The “Enable” phase isn’t about blocking traffic or setting up firewalls—that comes later. This pillar is focused entirely on data availability.
Zero Trust is a data-hungry architecture. To make real-time, “verify explicitly” decisions, your security tools need a constant stream of high-fidelity telemetry from every corner of your network. If your security stack is blind to certain traffic segments, your Zero Trust strategy isn’t just incomplete, it’s dangerous.
The Telnet Perspective: You can’t secure what you don’t monitor. Enabling Zero Trust means ensuring that every packet is captured, aggregated, and delivered to the tools that need it.
Why Visibility is the Foundation
Reputable frameworks like NIST SP 800-207 and the CISA Zero Trust Maturity Model emphasize that visibility and analytics are the cross-cutting capabilities that support every other pillar of security. Without the “Enable” phase, your organization faces several “Zero Trust Killers”:
- Encryption Blind Spots: While encryption is vital for privacy, it can hide malicious activity.
- Siloed Data: If your SIEM or NDR only sees a fraction of your traffic, its AI-driven “anomalies” are just guesses.
- Shadow IT: Unauthorized devices and applications can’t be “verified” if they are invisible to the network management layer.
The Toolkit: Network TAPs and Packet Brokers
In a Zero Trust architecture, “visibility” is not a passive luxury—it is the active fuel for your policy engine. To move toward an optimal maturity level, as defined by the CISA Zero Trust Maturity Model, an organization must collect as much information as possible about the current state of assets and communications. This requires two essential components: Network TAPs and Network Packet Brokers (NPBs).
While some organizations attempt to use SPAN (Switch Port Analyzer) ports for visibility, this often creates “Zero Trust Blind Spots.” SPAN ports are prone to packet loss under heavy load and frequently filter out the very error packets and anomalies that indicate a breach. To truly enable Zero Trust, you need a hardware-based foundation that guarantees 100% data fidelity.
Network TAPs: The Foundation of Ground Truth
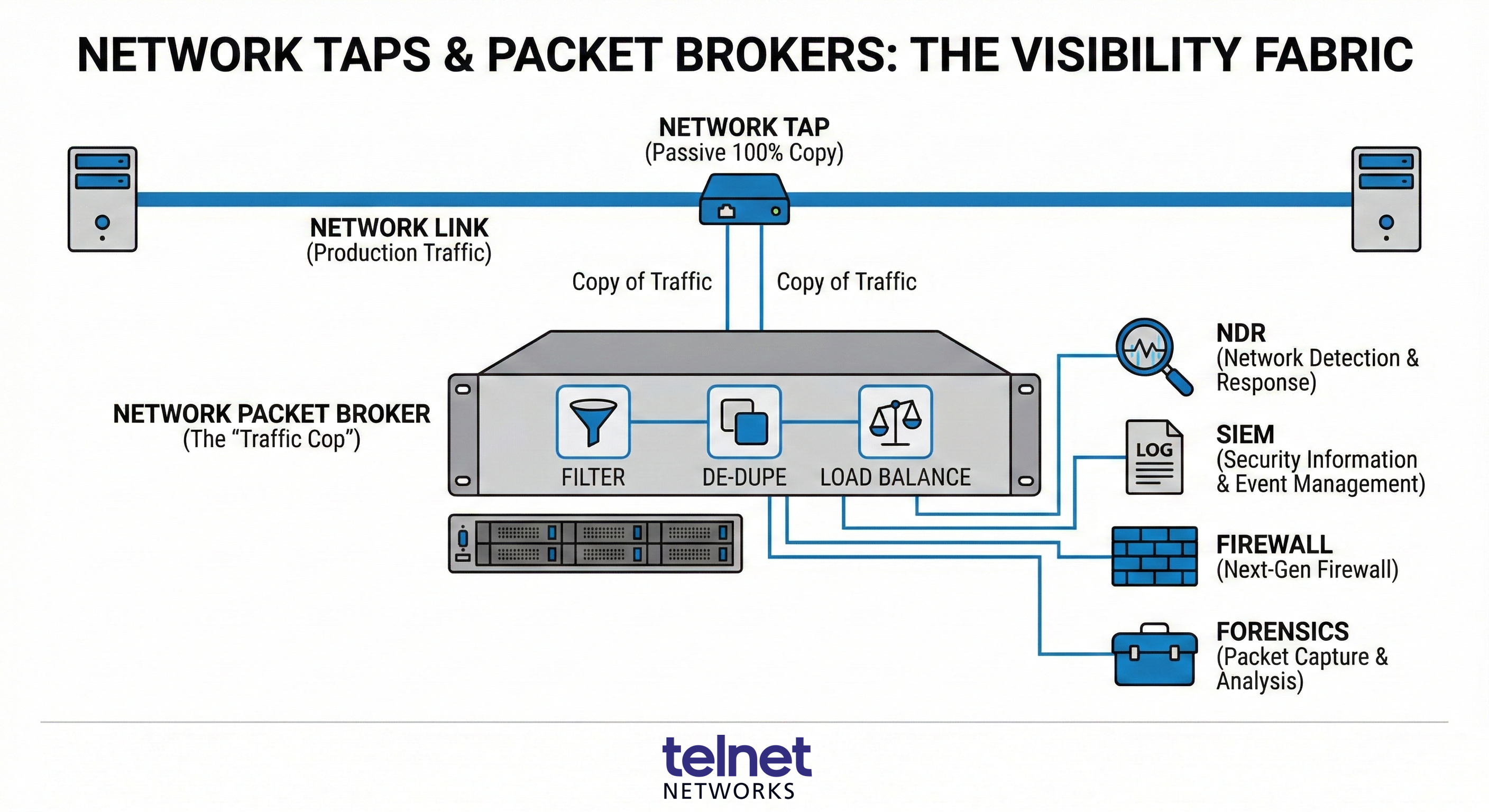
A Network TAP (Test Access Point) is a purpose-built hardware device that provides an exact, unaltered copy of all traffic flowing between two points in a network.
- 100% Capture: TAPs capture every bit, byte, and packet, including physical layer errors that traditional software-based monitoring might miss.
- No Performance Impact: Because they are passive or use “fail-safe” bypass technology, TAPs do not introduce latency or become a point of failure for the production network.
- Security by Design: Unlike managed switches, TAPs are “invisible” to the network and cannot be remotely hacked or misconfigured to stop traffic.
Network Packet Brokers: The Traffic Cop for Your Security Stack
Once the TAPs have captured the data, it must be delivered to your security tools (like NDR, SIEM, or DLP). However, sending 100% of raw traffic to every tool would quickly overwhelm them, leading to dropped packets and wasted licensing costs. Network Packet Brokers act as the “intelligence layer” between your network and your tools:
- Aggregation and Filtering: NPBs can take traffic from multiple TAPs and filter out irrelevant data (e.g., streaming video traffic) so your security tools only process what matters.
- De-duplication: If traffic is captured at multiple points, NPBs remove duplicate packets to ensure tools aren’t working twice as hard for the same insight.
- Load Balancing: High-speed 100G or 400G traffic can be distributed across multiple lower-speed security appliances, extending the life and ROI of your existing hardware.
Choosing the Right Partner for Your Industry
At Telnet Networks, we partner with the world’s leading visibility vendors to ensure we can match your industry or organization specific requirements. While all of our partners offer comprehensive portfolios of both TAPs and Packet Brokers, they each bring unique strengths to the table:
- Garland Technology: A leader in securing Critical Infrastructure and Government networks. With US-based manufacturing, Garland is often the preferred choice for Canadian organizations with strict compliance mandates in energy, finance, and healthcare where “Made in North America” and extreme reliability are paramount.
- Profitap: Focused on high-end Forensics and Deep Packet Capture. Based in Europe, Profitap serves over 1,000 clients globally, including many Fortune 500 companies. Their solutions are ideal for organizations that require specialized, portable, or high-density troubleshooting tools for R&D and complex incident response.
- Cubro Network Visibility: Known for providing a high ROI in Telecommunications and Data Centers. Cubro is a favorite for service providers and large enterprises looking for high-performance 4G/5G visibility without the burden of annual port or software licensing fees, significantly lowering the Total Cost of Ownership (TCO).
- Keysight Technologies: Offers perhaps the Broadest and Most Advanced Visibility Portfolio. Serving the aerospace, defense, and automotive sectors, Keysight’s “Vision” series is designed for the most complex hybrid-cloud environments, featuring advanced AI/ML stacks and context-aware application filtering.
By correctly implementing the Enable pillar with these tools, your organization creates a “visibility fabric” that removes the shadows where attackers hide. Only then are you ready for Pillar #2: Protect.
Moving Toward Maturity
Implementing the Enable pillar is the first step in a phased approach. It allows Canadian enterprises to move beyond “just keeping the bad guys out” to a proactive stance where they can find them quickly and limit damage when they do get in.
What’s Next? Establishing visibility is just the beginning. In our next article, we will explore Pillar #2: Protect, focusing on how to use that visibility to enforce least-privilege access and micro-segmentation. Stay tuned as we continue to build out the blueprint for a resilient, Zero Trust-enabled enterprise.


