Network visibility and security are two essential aspects of managing modern networks. Visibility focuses on monitoring and understanding traffic, devices, and user behaviour, while security actively protects networks from threats like malware and breaches. Both are critical, but they serve different purposes and complement each other to build stronger defenses.
Quick Takeaways:
- Network Visibility: Tracks network activity, identifies blind spots, and improves performance.
- Network Security: Protects against threats using tools like firewalls, encryption, and intrusion prevention systems.
- How They Work Together: Visibility identifies vulnerabilities, while security mitigates risks.
Quick Comparison:
| Aspect | Network Visibility | Network Security |
| Primary Function | Monitoring and analysis | Threat prevention and defense |
| Key Tools | TAPs, Packet Brokers, Monitors | Firewalls, IPS, Encryption |
| Response Type | Passive observation | Active threat mitigation |
| Focus | Performance and transparency | Defense and data protection |
Striking the right balance between visibility and security ensures both smooth operations and robust protection. Read on to learn how these two work together and the tools and strategies to implement them effectively.
6 Ways Network Visibility Can Optimize Your Network
Defining Network Visibility
Network visibility refers to the ability to track and understand everything happening within a network, including data movement, connected devices, applications, and user actions.
What Network Visibility Does
With network visibility, IT teams can improve performance by spotting bottlenecks and ensuring compliance by monitoring sensitive data access and protection. In hybrid work setups – where 86% of IT teams now manage both remote and in-office operations – visibility offers a unified perspective that helps departments collaborate effectively [2].
This not only improves how the network runs but also strengthens security measures.
Tools That Provide Network Visibility
To achieve network visibility, organizations use several essential tools:
- Network Packet Brokers (NPBs): These tools streamline network traffic, manage load balancing, and eliminate blind spots to keep operations running smoothly [1].
- Test Access Points (TAPs): TAPs monitor network activity without interrupting normal operations, allowing for continuous data collection and analysis [1].
- Performance Monitoring Solutions: These platforms analyze traffic patterns, application performance, user behaviour, and resource usage [2].
While visibility gives organizations a clear picture of network activity, security tools ensure that this knowledge is used to defend against threats.
Defining Network Security
Network security refers to the tools, practices, and protocols designed to shield networks from unauthorized access, cyberattacks, and data breaches. While network visibility focuses on monitoring, security takes a proactive role in defending systems and protecting sensitive information.
Components of Network Security
Effective network security depends on several key elements working in unison. Visibility tools supply the crucial data these components need to identify and address threats quickly:
- Firewalls: Serving as the first line of defense, firewalls filter traffic based on established security rules. For example, Palo Alto Networks‘ Next-Generation Firewalls (NGFW) can stop over 95% of zero-day malware before it infiltrates a network.
- Access Control: Ensures that only authorized users can access specific resources, protecting critical data from both internal and external risks.
- Intrusion Prevention Systems (IPS): These systems use machine learning to detect and block suspicious activities, cutting response times from hours to just minutes.
- Encryption: Encrypting data strengthens its protection and can lower breach-related costs by an average of $1.4M, according to IBM’s 2023 findings.
When these components are combined, businesses can better address the wide variety of threats targeting their networks.
Common Security Threats
Modern networks face increasingly advanced threats, making strong defenses more important than ever:
| Threat Type | Impact & Prevention |
| Malware Attacks | Average cost of $2.6M; mitigated with antivirus tools and endpoint protection. |
| Phishing Campaigns | Target 83% of organizations; countered with email filtering and employee training. |
| Insider Threats | Account for 34% of breaches; reduced with strict access controls and continuous monitoring. |
The growing complexity of networks, fueled by IoT devices and hybrid work environments, expands the potential attack surface. This underscores the need to integrate visibility tools with security measures for a well-rounded defense plan.
Differences Between Network Visibility and Security
Network visibility and security are two key aspects of managing enterprise networks. While they work hand-in-hand, they serve different purposes in keeping networks running smoothly and securely.
Objectives of Visibility and Security
The goals of network visibility and security are distinct, yet they complement each other. Network visibility focuses on observing and understanding how the network behaves. It provides real-time insights into traffic flows and performance metrics. On the other hand, security is all about preventing threats and safeguarding the network. When combined, visibility enhances security by offering the insights needed to tackle modern threats more effectively.
How Visibility Supports Security
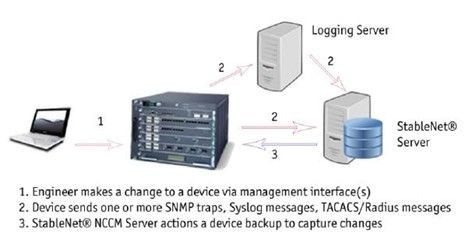
Visibility tools lay the groundwork for stronger security. With hybrid workforces becoming the norm, managing distributed networks requires seamless integration of visibility and security tools. For example, visibility tools can spot vulnerabilities, enabling security measures to act swiftly and accurately.
This partnership is especially important when dealing with encrypted traffic. Integrated solutions make it easier to detect threats that might otherwise stay hidden in encrypted communications.
Comparing Tools and Technologies
The tools used for visibility and security reflect their specific roles, but they work together to create a robust defense:
| Aspect | Visibility Tools | Security Tools |
| Primary Function | Monitoring and analyzing networks | Preventing and addressing threats |
| Key Technologies | TAPs, Packet Brokers, Traffic Analyzers | Firewalls, IPS, Antivirus Software |
| Data Handling | Collects and studies traffic | Filters and blocks malicious traffic |
| Response Type | Passive observation and reporting | Active threat mitigation |
| Implementation Focus | Performance and transparency | Defense and data security |
Balancing Visibility and Security
Combining Visibility and Security Solutions
Modern enterprise networks are becoming increasingly complex, making it crucial to align visibility and security efforts.
Network Packet Brokers (NPBs) play a key role in this alignment by filtering traffic, easing processing demands, and increasing the accuracy of threat detection. This is especially helpful in high-speed or encrypted environments. For instance, financial institutions often pair TAPs with SIEM systems to cut down on response times and enhance detection capabilities.
Merging visibility and security tools helps organizations detect threats earlier, reduce blind spots, improve response times, and meet compliance requirements.
Implementation Tips
To get the most out of integrated solutions, a well-thought-out implementation strategy is essential.
Continuous Monitoring Strategy
Focus your monitoring efforts on the most critical parts of your network to stay ahead of potential threats.
Smart Tool Integration
| Integration Aspect | Implementation Approach | Expected Outcome |
| Traffic Analysis | Use NPBs with load balancing | Better performance of security tools |
| Threat Detection | Pair TAPs with IDS/IPS | Faster identification of threats |
| Performance Monitoring | Set up automated alerts | Quicker response times |
| Compliance Tracking | Activate continuous audit logging | Improved adherence to regulations |
Cross-Team Collaboration
Technology alone isn’t enough – effective teamwork is just as important. Encourage IT and security teams to collaborate using shared dashboards and centralized data. This ensures a unified approach to managing both visibility and security within the network.
Regular audits of your network infrastructure are crucial to identify and address any blind spots or performance issues. This is particularly important, as 67% of businesses struggle with visibility gaps in their data protection efforts [2].
Conclusion
Network visibility and security are key components of modern network management, working together to create safer, more reliable systems. As networks become more complex and threats grow more advanced, combining these two elements has never been more important.
Data underscores the need to eliminate blind spots in network oversight. Organizations that successfully integrate visibility and security tools build stronger defenses against ever-changing threats. These tools, when used together, can achieve outcomes that neither could accomplish on its own.
As networks expand, particularly across distributed systems, blending visibility and security becomes essential. Tools like Network Packet Brokers (NPBs) and TAPs offer the monitoring capabilities needed to maintain oversight, while security solutions use this data to guard against risks. This partnership is especially critical in environments where networks span multiple locations and systems.
Clear visibility plays a crucial role in executing effective security strategies, particularly when addressing supply chain risks and managing widespread resources. The tools explored in this article – TAPs, NPBs, and security solutions – illustrate how these two areas complement one another in real-world applications.
To manage networks effectively, organizations must strike a balance between visibility and security. This approach doesn’t just identify threats – it helps prevent and address them. By treating these elements as cooperative rather than competing priorities, businesses can create more resilient networks that meet both performance and protection demands.
FAQs
What does a network tap do?
A Network TAP (Test Access Point) duplicates incoming and outgoing data packets for analysis without interfering with network traffic. TAPs are crucial for monitoring because they:
- Provide full data access: Capture every data packet for in-depth analysis.
- Ensure reliability: Keep functioning even during power outages, maintaining network operations.
How does network visibility improve security?
Network visibility helps organizations understand traffic patterns and identify potential threats. By offering detailed insights, it allows for quicker detection and response to incidents. This is especially important given that 54% of organizations struggle to pinpoint vulnerabilities within their supply chains [2].
What is the function of Network Packet Brokers?

Network Packet Brokers (NPBs) streamline monitoring by filtering traffic, minimizing data duplication, and directing relevant information to security tools. They complement TAPs to ensure no blind spots exist in network monitoring [1].
How can organizations enhance network visibility?
Organizations can boost visibility by reworking their monitoring systems, collecting more data, decrypting traffic for deeper analysis, and leveraging machine learning to spot threats [2][3].
When combined effectively, these strategies help strengthen both visibility and security in modern network management.