Security starts with awareness, but what happens when critical traffic slips through unnoticed? For security teams and network administrators alike, network visibility isn’t just a luxury—it’s a necessity. As threats become more sophisticated, ensuring complete, real-time access to network traffic is the first step in defending against malicious activity. This is where technologies like Network TAPs, Network Packet Brokers, and Bypass Switches come into play.
What is Network Visibility?
Network visibility refers to the ability to monitor all traffic flowing across a network—north-south (between users and data centers) and east-west (between internal systems, users and endpoints). Without it, blind spots emerge, leaving room for attackers to move undetected.
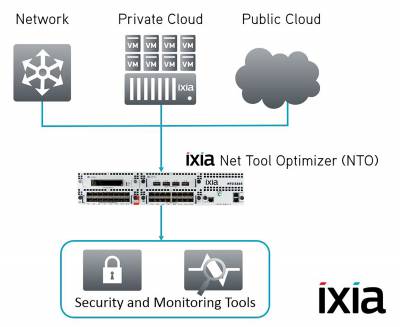
Visibility tools like Network TAPs (Test Access Points), Network Packet Brokers (NPBs), and Bypass Switches are the foundation for building a resilient, secure, and high-performance network. Each plays a unique role in feeding security appliances the data they need to function effectively.
Network TAPs: Your First Line of Insight
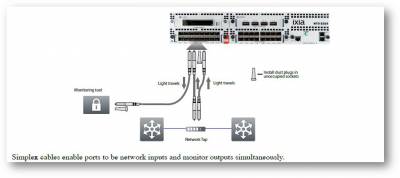
Network TAPs (Test Access Points) are dedicated hardware devices designed to deliver a real-time, unfiltered copy of network traffic. Placed in-line between network segments, TAPs allow all data to flow through uninterrupted while simultaneously duplicating that traffic for monitoring and security tools. Unlike other methods that may filter or miss packets under load, TAPs provide a complete and accurate view of every packet traversing the network—ensuring your tools receive 100% of the data, with zero interference, loss, or blind spots.
Security Use Cases:
Intrusion Detection Systems (IDS) rely on clean, complete traffic to detect anomalies.
Forensics and packet capture solutions use TAPs to store traffic for analysis after an incident.
Decryption appliances can tap into SSL/TLS sessions for deep inspection.
Network TAPs are available from vendors like Garland Technology, Cubro, Profitap and Keysight.
Network Packet Brokers: Smart Traffic Management
Gaining visibility is just the first step—managing that traffic effectively is where the real challenge begins. This is where Network Packet Brokers (NPBs) come into play. These smart, purpose-built devices aggregate traffic from multiple sources, then filter, de-duplicate, and reformat it before sending it to your security and monitoring tools.
By delivering only the relevant data in the optimal format, NPBs reduce tool overload, eliminate unnecessary noise, and ensure that each system receives precisely what it needs to operate at peak efficiency.
Security Use Cases:
Traffic filtering: Send only relevant data to specific security appliances to reduce overload.
Load balancing: Distribute traffic across multiple tools for redundancy and scalability.
Packet deduplication and header stripping: Eliminate noise and unnecessary metadata that can bog down inspection.
Bypass Switches: High Availability for In-line Security
Bypass Switches, unlike TAPs and Network Packet Brokers, are purpose-built for in-line security tools—such as firewalls, intrusion prevention systems (IPS), and secure web gateways—that actively inspect and control live traffic. Because these tools sit directly in the path of network data, any failure or maintenance downtime can disrupt the flow of traffic and impact availability. Bypass switches solve this challenge by intelligently redirecting traffic around the in-line device if it becomes unresponsive or needs to be taken offline. This ensures continuous uptime, minimizes risk, and allows security teams to maintain and upgrade in-line defenses without interrupting business operations.
Security Use Cases:
Fail-safe failover: If an in-line appliance fails or is taken down for maintenance, bypass switches keep traffic flowing uninterrupted.
Heartbeat monitoring: Ensure that in-line tools are healthy and responsive.
Scheduled updates and maintenance windows: Perform patching or upgrades without interrupting traffic.
The Power of an Integrated Visibility Fabric
Individually, TAPs, Brokers, and Bypass Switches solve specific problems. Together, they form a visibility fabric—a unified, scalable approach to traffic monitoring that supports both performance and security initiatives.
If you’re struggling with visibility gaps or underperforming security tools, it’s time to rethink your monitoring strategy. Contact the Telnet Networks sales team to learn how we can help you deploy the right mix of Network TAPs, Network Packet Brokers, and Bypass Switches from market leading and innovative partners like Garland Technology, Cubro, Profitap and Keysight to secure your infrastructure from the ground up.