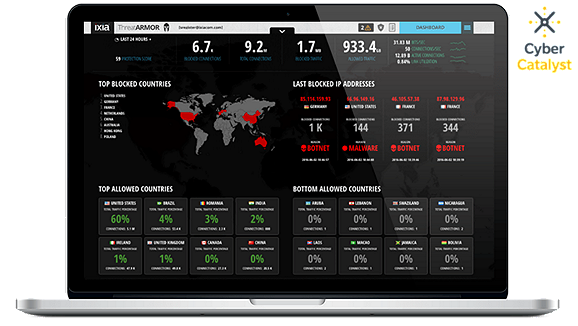
Reduce your attack surface, prevent SIEM alert fatigue, and block up to 80% of malicious traffic
Stop Attackers in their Tracks
Reduce Your Attack Surface and Prevent Alert Fatigue
Alert fatigue is a critical concern for security operations. Attacks are preventable, but the Ponemon Institute reports that only 29% of security alerts are ever investigated. SecOps teams work tirelessly, but the sheer volume of alarms from security information and event management (SIEM) tools is too much to manage — and vital clues are often missed.
You need to reduce your attack surface, and stop threats from ever triggering SIEM alerts in the first place. That’s why SecOps teams trust ThreatARMOR, a threat intelligence gateway, to stop attackers in their tracks. While bad actors may circumvent firewall filters, ThreatARMOR offers a more resilient defense — blocking threats by location, not behavior.
A central component of Keysight's Security Operations Suite, ThreatARMOR enables you to do all this and more:
- Block 80% of hostile traffic, botnets, and ransomware.
- Achieve a 15x return on investment in a single year.
- Reduce SIEM alarms and SecOps alert fatigue.
- Optimize operations with full line-rate performance.
- Stay ahead of attacks with continuous threat updates.
- Improve resiliency with turnkey bypass switch integration.
- See on-screen proof of malicious activity for blocked sites.
- Deploy in just 30 minutes, with no ongoing maintenance.
ThreatARMOR isn't a Firewall. It's Your First Line of Defense.
Next-gen firewalls (NGFWs) are great at deep packet inspection and threat detection, but they are not optimized for blocking malicious, hijacked, and untrusted IP addresses at massive scale. Even if they can import a threat intelligence feed, trying to block tens of millions of IP addresses isn't possible without significant latency and impact to performance. ThreatARMOR complements NGFWs by offloading massive-scale blocking so that they can allocate more resources to content inspection, user policies, VPN termination, and other features while generating fewer security alerts.
Watch the video to learn more about how threat intelligence gateways like ThreatARMOR work.
ThreatARMOR Wins Coveted Marsh Cyber Catalyst Designation
Leading insurers designate it effective in reducing cyber risk.
The Cyber Catalyst by MarshSM program is designed to provide organizations with greater clarity and confidence in choosing cybersecurity products in the face of growing uncertainty. The program enables customers that adopt designated technologies to be considered for enhanced terms and conditions on cyber insurance policies from participating insurers.
With this designation, you can rest assured ThreatARMOR doesn't just help you reduce your attack surface and prevent alert fatigue — it also enables you to manage cyber risks and financial liabilities with confidence.
 Block Attackers With Industry-Leading Threat Intelligence
Block Attackers With Industry-Leading Threat Intelligence
The world leader in application and security testing, our Application and Threat Intelligence (ATI) Research Center keeps ThreatARMOR updated with the latest threats. Our database contains more than 50 million records, and millions of new threats are analyzed and cataloged each month.
Our ATI research center supplies ThreatARMOR with an always-on stream of geolocation and threat intelligence — individually validating every single blocked IP address, every single day. Detailed Rap Sheets provide clear, on-screen proof of malicious activity for all blocked sites to mitigate the risk of false positives.
Prevent Malware. Protect Your Network.
Malware relies on network communication to download instructions and transmit sensitive data. But ThreatARMOR™ makes it easy to stay a step ahead. By automatically blocking network probes, phishing clicks, and all traffic to and from untrusted countries, you can dramatically reduce your risk of zero-day ransomware mutations — all while reducing malicious connections by as much as 80%.
Additionally, ThreatARMOR™ easily combines with our range of Bypass Switches to enhance the effectiveness, availability, and resiliency of your cyber defenses.
 Security Operations Services
Security Operations Services
No time to deploy and manage another tool? No problem.
Are you looking to improve security operations, but lacking the personnel to make it happen? We get that. When your team is fighting fires all day, it can be hard to imagine making time for anything else.
That's why we offer a full range of managed security operations services. Whether you're looking for monthly assessments or a one-time engagement, we can help you do all this and more:
- Measure the effectiveness of your overall security posture.
- Identify and fix vulnerable misconfigurations with actionable remediations.
- Assess and troubleshoot specific tool deployments or threat vectors.
- Improve SIEM efficiency by blocking up to 80% of malicious network traffic.

