-
Call Us:1.800.561.4019
Newsletter
For a Free Quote...
Latest Blog Posts
Blog Categories
Telnet Networks News
A Life-Cycle View of Network Security
With the amount of sustained security attacks launched at enterprises over the last five-plus years, network security has become an increasingly important topic—right along with how new methodologies and technologies can be used to combat the proliferation of attacks.
As daily news stories document, enterprises are struggling with preventing breaches in their network security. According to Symantec, 2013 was the “Year of the Mega Breach.” The total number of breaches was 62% higher than the level set in 2011 (which Symantec had previously cited as the “Year of the Data Breach”). Another interesting data point I found from Arbor Networks is that 25% of companies are seeing more than 21 attacks per month. Also, if you have a cloud environment then the Ponemon 2014 Data Breach: The Cloud Multiplier Effect report predicts that you are three times more likely to be breached than other companies.
Not only do breaches affect the company brand, but economic losses continue to mount as well. The threat is credible and verifiable. In general, you have a close to 60% chance of being attacked this year—that’s according to a 2014 report from Neustar.
 Ixia believes that a life-cycle approach can help enterprises strengthen their security defenses and create resilient security architectures. The basic concept is that every network has different stages (a lifecycle) that it goes through during the course of its usable life. During those different stages there are distinct activities that should take place that will help strengthen the network. When those activities are implemented correctly, at the proper time, your proactive and reactive capabilities will be as sharp as possible. You can view a webinar on this topic if you want.
Ixia believes that a life-cycle approach can help enterprises strengthen their security defenses and create resilient security architectures. The basic concept is that every network has different stages (a lifecycle) that it goes through during the course of its usable life. During those different stages there are distinct activities that should take place that will help strengthen the network. When those activities are implemented correctly, at the proper time, your proactive and reactive capabilities will be as sharp as possible. You can view a webinar on this topic if you want.
Let’s back up for a minute though. In general, IT people are working to protect their networks. Conventional wisdom says you should invest in securing your access and architecture vulnerabilities.
This means that these are probably the main thrust of your security focus, correct?
- Firewalls
- Intrusion Prevention Systems
- Intrusion Detection Systems
- Data Loss prevention systems
- Penetration testing
- Forensic recorders
- SIEMs
And for the most part, the products do what they say they should do. So why is Ixia advocating that you should look at network security differently? Mainly because what’s being practiced now doesn’t really work that well, or we wouldn’t be seeing all of the breaches that we are in the enterprise.
So, what’s the problem? The first problem is that focusing on access and vulnerabilities provides only a microscopic view. This leads to point “solutions” that tend to have multiple problems like:
- Higher overall costs as you add components piecemeal
- Poor solution scalability
- “Clusters of junk” that don’t work well together because the solution part usually ends up being missed
If you step back and take and also take a systems approach, or macroscopic view, you can get additional, critical details. For instance:
- A systems view provides a cohesive architecture that can maximize the benefits of visibility like the following:
- With a faster MTTR, you can see an up to 80% reduction in your resolution times
- Application filtering can save bandwidth and tool processing cycles
- Automation capabilities, which can provide a faster response to anomalies without user administration
- A systems view also provides for process alignment
- A systems view provides documented due diligence to limit the costs associated with a breach
So, there is a better way forward. Before, we just had Access and Architecture Vulnerability. Let’s add the other components. This means that typical network security activities should focus on the following:
- Access
- Policies and procedures
- Architecture performance (vulnerability and resilience)
- Monitoring and auditing
For instance, policies and procedures should be inserted into the security process as well. Unfortunately, this doesn’t always happen. In fact the NTT Group, in their 2014 Global Threat Intelligence Report, found that over 75% of companies studied had no incident response plan. And this wasn’t just small companies. This included many of the Fortune 100 companies.
While a lack of processes may make it easier to implement changes in the network, it has at least two serious issues associated with it. First, lack of processes help create security risks by removing change approval and documentation procedures. Second, the lack of processes usually results in longer time frames to isolate problems within the network.
In addition to securing architecture vulnerabilities, there needs to be an emphasis on analyzing a security architecture’s performance and its ability to respond in a resilient manner to security threats and breaches. You want to prevent a breach, but once one happens you need the network to adapt to the threat and remediate the threat as fast as possible. You also want your defenses to be as strong as possible against attacks but be flexible enough to let good traffic pass through.
Monitoring and auditing are also extremely important but often overlooked—which is very strange. If you can’t see the threat, how are you going to respond to it? Once you combine the security architecture with the visibility architecture, you will equip yourself with the necessary tools to properly visualize and diagnose the problems on your network.
One key idea is to integrate your security and visibility architectures. This will help you to optimize your network in the following ways:
- Better data to analyze security threats
- Better operational response capabilities against attacks
- The application of consistent monitoring and security policies
Remember, the key is that by integrating the two architectures you’ll be able to improve your root cause analysis. This is not just for security problems but all network anomalies and issues that you encounter.
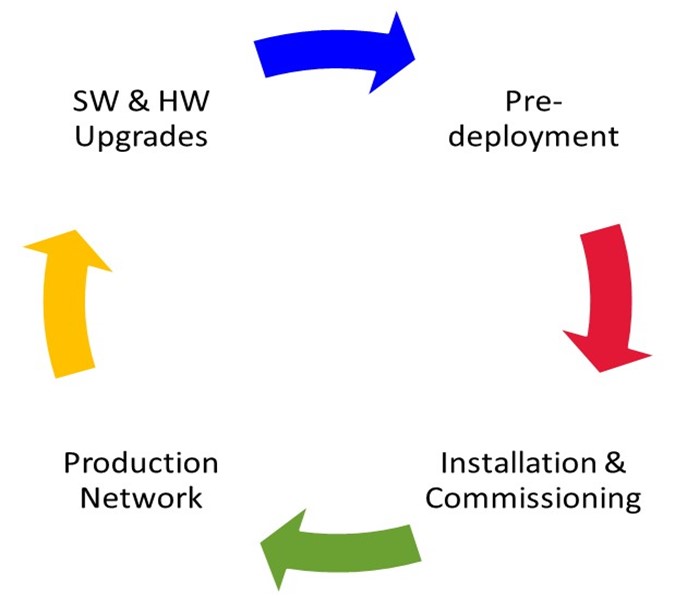
Now, let’s return to the life-cycle approach. Just as the seasons change during the course of a year, your network has different needs and attributes during the four main lifecycle stages of its usable life. Each of these life-cycle stages may touch on one or more of the four groups of activities I mentioned before (access, policies and procedures, architecture performance, and monitoring).
From a network equipment deployment perspective, there are typically five distinct phases:
- Pre-deployment (usually in a lab)
- Installation and commissioning (where the equipment is installed and turned up in the field)
- Production network (which is the steady state operational phase for the equipment/network)
- Software and hardware upgrades (which is the change management phase)
- End of life
Since “end of life” doesn’t really pertain to our discussion, we’ll leave it out and only focus on the other four phases. There shouldn’t be anything radical here. The only new concept should be that each of these phases has distinct activities associated with them. All too often people forget or dismiss that concept. Once they do, they start to miss activities and steps that create the process problems and architecture vulnerabilities we talked about earlier. Understanding these four lifecycle stages and their different security needs will minimize the threat to your network.

As I just mentioned, each of the four stages has a separate contribution to overall network security. This is indicated in the blue text in the adjacent life-cycle diagram. Basically,
- During the pre-deployment stage, you are trying to validate whether your solution will solve all of your requirements.
- The purpose of the installation and commissioning stage is to check that the final solution setup is deployed correctly for your network.
- The production stage is concerned with constant monitoring and testing for aberrant behavior.
- Upgrades, the last stage, is focused on testing any changes before you introduce them into the network. Basically, you want to prevent as many self-inflicted injuries as you can.
Additional Resources:
Network life-cycle eBook: How to Secure Your Network Through Its Life Cycle
Network life-cycle webinar: Transforming Network Security with a Life-Cycle Approach
Visibility architecture security whitepaper: The Real Secret to Securing Your Network
Security architecture whitepaper: How to Maximize IT Investments with Data-Driven Proof of Concept (POC)
Security solution overview: A Solution to Network Security That Actually Works
Cyber range whitepaper: Accelerating the Deployment of the Evolved Cyber Range
Thanks to Ixia for the article.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.




Comments